

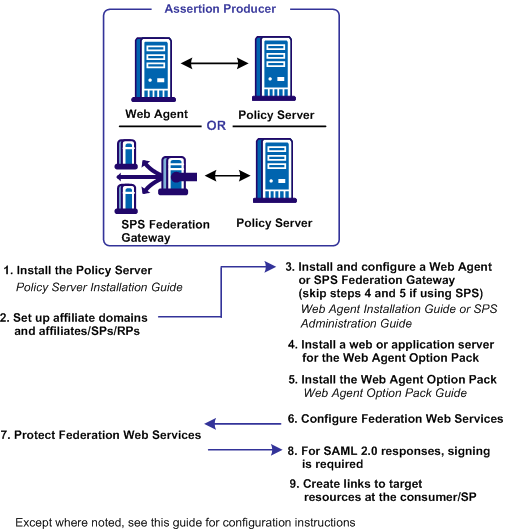
The following illustration shows a SAML 1.x Producer, SAML 2.0 Identity Provider, or WS-Federation Account Partner setup.
Note: The SPS federation gateway can replace the Web Agent and Web Agent Option Pack to provide the Federation Web Services application functions. For information about installing and configuring the SPS federation gateway, see the Secure Proxy Server Administration Guide.
The setup at the asserting party is as follows:
See the Policy Server Installation Guide.
For information about the session store, see the Policy Server Administration Guide.
The session store is required only for artifact single sign-on because the session server stores an assertion before it is retrieved.
This user directory must contain the users for which assertions are generated.
Before you set up Federation Web Services, you establish affiliate domains and add the sites that consume assertions to the affiliate domains. The affiliate domains identify the partners to the site generating the assertions.
At the asserting party
There must be a one-to-one correspondence between a relying party and each object added to the domain.
To do this task:
The Web Agent is a required component in a CA SiteMinder® federation network. Install a Web Agent on a web server or install an SPS federation gateway, which has an embedded web agent.
At the asserting party, set up the following components:
For instructions, see the Web Agent Installation Guide.
For instructions, see the Secure Proxy Server Administration Guide.
If you are implementing legacy federation with a Web Agent and Web Agent Option Pack, install the Web Agent Option Pack. Install this component on a web or application server.
At the asserting party:
The Web Agent Option Pack supplies the Federation Web Services application, which is a required component for CA SiteMinder® legacy federation.
At the asserting party:
For instructions, see the Web Agent Option Pack Guide.
For the supported JDK version, log on to the Technical Support site and search for the CA SiteMinder® Platform Support Matrix for the release.
Note: The SPS federation gateway can replace the Web Agent and Web Agent Option Pack to provide the Federation Web Services application functions. For information about installing and configuring the SPS federation gateway, see the Secure Proxy Server Administration Guide.
The Federation Web Services application is installed on the server with the Web Agent Option Pack or the SPS federation gateway.
To configure Federation Web Services at the asserting party
On the SPS federation gateway, Federation Web Services is already deployed.
The AffWebServices.properties file contains the initialization parameters for Federation Web Services. This file is located in the one of the following directories:
Represents the installed location of the Web Agent
Represents the installed location of the SPS federation gateway
http://fqhn:port_number/affwebservices/assertionretriever
Defines the fully qualified host name.
Defines the port number of the server where the Federation Web Services application is installed.
For example:
http://myhost.ca.com:81/affwebservices/assertionretriever
If Federation Web Services is operating correctly, you see the following message:
Assertion Retrieval Service has been successfully initialized. The requested servlet accepts only HTTP POST requests.
This message indicates that Federation Web Services is listening for data activity. If Federation Web Services is not operating correctly, you receive a message that the Assertion Retrieval Service has failed. If the test fails, look at the Federation Web Services log.
When you install the Policy Server, CA SiteMinder® creates policies for the Federation Web Services (FWS) application. The FWS application is installed with the Web Agent Option Pack. For a few federation features, the relying party needs permission to access the protected FWS service. Adding a relying partner to a policy is a task you do only at the asserting party.
For example, for HTTP-Artifact binding for single sign-on, a policy protects the service from which CA SiteMinder® retrieves an assertion. For CA SiteMinder® to retrieve the assertion for a specific relying partner, that partner must be added as a user to the policy that protects the service.
Grant access to specific FWS policies that apply to features configured for your federation partnership.
Signing SAML POST responses is a SAML specification requirement. To sign SAML POST responses, add a private key and certificate to the certificate data store at the asserting party.
For instructions on importing keys and certificates into the data store, see the Policy Server Configuration Guide.
Go to one of the following:
At the SAML 1.x producer, create pages that contain links which direct the user to the consumer site. Each link represents an intersite transfer URL. The user has to visit the intersite transfer URL, which sends a request to the producer-side Web Agent. The user is then redirected to a consumer site.
The link that the user selects at the producer must contain certain query parameters. These parameters are part of an HTTP GET request to the producer Web Agent.
For the SAML artifact profile, the syntax for the intersite transfer URL is:
http://producer_site/affwebservices/public/intersitetransfer?SMASSERTIONREF= QUERY&NAME=affiliate_name&TARGET=http://consumer_site/target_url?query_parameter_name%3Dquery_parameter_value%26query_parameter_name%3Dquery_parameter_value&SMCONSUMERURL=http://consumer_site/affwebservices/public/samlcc&AUTHREQUIREMENT=2
Specifies the server and port number of the system hosting the Web Agent Option Pack or the SPS federation gateway, depending on which components are installed in your federation network.
Specifies the server and port number of the system hosting the Web Agent Option Pack or the SPS federation gateway, depending on which components are installed in your federation network.
For the SAML POST profile, the syntax for the intersite transfer URL is:
http://producer_site/affwebservices/public/intersitetransfer?SMASSERTIONREF= QUERY&NAME=affiliate_name&TARGET=http://consumer_site/target_url
Specifies the server and port number of the system hosting the Web Agent Option Pack or the SPS federation gateway, depending on which components are installed in your federation network.
Specifies the server and port number of the system hosting the Web Agent Option Pack or the SPS federation gateway, depending on which components are installed in your federation network.
Note: The SAML POST profile does not use SMCONSUMERURL and AUTHREQUIREMENT parameters. However, if you include one of these parameters in the intersite transfer URL, include the other parameter.
If a user visits the Identity Provider before going to the Service Provider (POST or artifact binding), initiate an unsolicited response at the Identity Provider. To initiate an unsolicited response, the Federation Web Service application and assertion generator accept an HTTP Get request with a query parameter. This query parameter indicates the Service Provider ID for which the IdP generates the response.
For SAML 2.0 artifact or post profile, the syntax for the link is:
http://IdP_server:port/affwebservices/public/saml2sso?SPID=SP_ID
Identifies the web server and port hosting the Web Agent Option Pack or SPS federation gateway.
Service Provider ID value. The entity ID is case-sensitive. Enter it exactly as it appears in the Administrative UI.
Add the ProtocolBinding query parameter to this link depending on which bindings are enabled.
Note: You do not need to HTTP-encode the query parameters.
You can also initiate single sign-on at the Service Provider.
To initiate WS-Federation single sign-on, a user clicks on a page with a hard-coded HTML link. This HTML link directs the browser of the user to the single sign-on service at the Account Partner. The Account Partner then redirects the user to the Resource Partner.
The link that initiates single sign-on can be included at any site, but it must always first direct the user to the Account Partner.
The syntax for the link is:
https://AP:port/affwebservices/public/wsfedsso?wa=wsignin1.0&wtrealm=RP_ID
Specifies the server and port number of the system at the Account Partner. The system is hosting the Web Agent Option Pack or the SPS federation gateway, depending on which component is installed in your federation network.
Note: You do not need to HTTP-encode the query parameters.
|
Copyright © 2014 CA.
All rights reserved.
|
|