

The Policy Server assumes that a user is authenticated and authorized against the same user directory. However, users can be authenticated against one directory, and authorized against a separate directory. This feature is called directory mapping.
You can map a central directory that stores authentication information with separate distributed user directories that store authorization information. The authorization directories are associated with particular network applications. The mappings locate authenticated users in separate authorization directories.
Note: Directory mapping does not support Impersonation. The user being impersonated, must be uniquely present in the authentication directories that are associated with the domain or the impersonation fails.
Mapping from an authentication directory to an authorization directory is a three-step process.
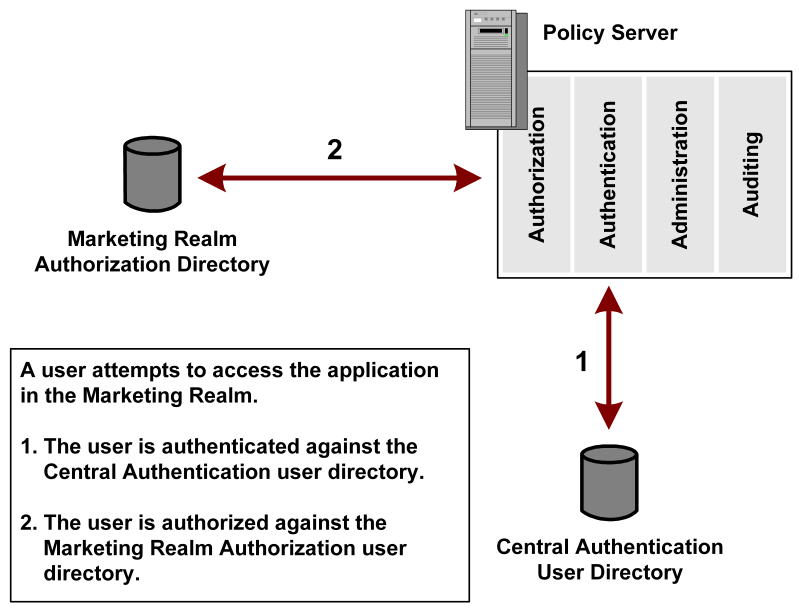
For example, all the users in the company are authenticated against one central user directory. The marketing organization is authorized against a separate user directory. You can configure a directory mapping between the authentication and the marketing authorization user directories then create a realm for the marketing application. The realm uses the authorization directory defined in the mapping. When a user tries to access the marketing application, the user is authenticated against the central user directory and authorized against the marketing user directory.
The following diagram shows this example.
Identity mappings let you configure multiple target user directories and use custom search criteria. This configuration gives you flexibility in setting up your environment.
There are two types of identity mappings:
A directory mapping for authenticating users against one directory and authorizes users against a different directory.
A directory mapping for authenticating users against one directory and validating users against a different directory. An authentication user directory that is connected to one Policy Server is mapped to a validation user directory that is connected to a different Policy Server.
Identity mappings do not require existing user directory connections.
There is a legacy method for directory mapping called Legacy (Auth/Az and AuthValidate) Directory Mappings. This legacy method is still available in this release, and any existing legacy mappings continue to work in the same way.
For legacy directory mappings, the user directory connections to the Policy Server must exist for the authentication directory and the authorization or validation directory.
|
Copyright © 2014 CA.
All rights reserved.
|
|