

Domino servers sometimes require special CA SiteMinder® agent parameters. These parameters are used only for Domino servers unless otherwise indicated. Use the topics in the following categories to protect your Domino resources:
The Domino Application Server is a messaging and Web application platform that offers secure access for Lotus Notes clients. The Domino Web Agent protects only the HTTP interface of the Domino Application Server, controlling access to HTML, JAVA, CGI, and other Web resources, such as Notes served over the web. It does not protect the Notes server.
The following illustration shows how the Domino Web Agent integrates with the Domino server.
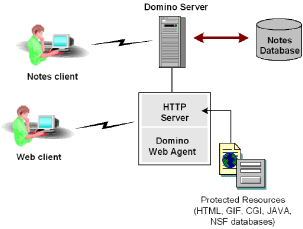
Domino stores data in groups of Notes databases. Resources in a Notes database can be a variety of objects, such as documents, views, forms, and navigators. These objects can include text, video, graphics, and audio content.
Notes objects are opened using a URL. To make Notes objects available for the Web, Domino dynamically creates Web pages from the objects in the Notes database. In the case of database views, Domino also creates URL links to the documents in a view. The dynamic creation of pages from the Notes database provides users with the most current information.
Access to resources on a Domino server is based on the URL. Domino servers use a specific URL syntax.
Domino servers can interpret standard URLs, such as one shown in the following example:
http://www.example.com/index.html
Domino URL commands can use the following syntax:
http://host/database.nsf/Domino_object?Action_Argument
Indicates the DNS entry or IP address of the server.
Specifies the database file name with the path relative to the notes \data directory or the database Replica ID.
Specifies the object in the database, for example, a view, document, form, or navigator.
Identifies the operation that performed on the Notes object. For example: ?OpenDatabase, ?OpenView, ?OpenDocument, ?OpenForm, ?ReadForm, ?EditDocument. If no action is specified in the URL, the default is used.
Default: ?Open.
Defines how the Domino server delivers an object. For example, if the action and argument is?OpenView&Expand=5, this argument specifies the number of rows displayed in an expanded format.
The following example shows a URL to access a view in a Notes database named financials.nsf:
http://www.example.com/financials.nsf/reports?OpenView
One of the Notes database conventions is to create aliases for objects. For example, the alias might identify a resource by its Notes ID or Replica ID instead of the object name. Using aliases makes programming easier for developers because the names of the Notes resources can change without requiring code changes.
The following Domino URLs access the same resource though the resource is identified by its aliases:
Regardless of how a resource is identified, the Domino Web Agent converts all Domino naming conventions into a standard URL based on the name of the database resource. This simplifies data entry into the CA SiteMinder® policy store.
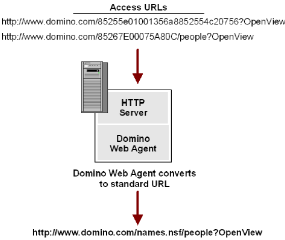
For example, the following Domino URLs are pointing to the people view in the names.nsf database. The database and view are referred to by Replica ID and Notes ID:
The Domino Web Agent converts these URLs to a standard URL, as follows:
The following illustration shows the conversion of aliases to a named object.
The Domino Web Agent uses all the standard Web Agent settings to do the following:
You can configure these centrally at the Policy Server or locally in the Agent configuration file.
In addition to the standard functions, there are Domino-specific parameters you can set.
In addition to the standard Web Agent settings, there are specific Domino configuration parameters that you can set only for the Domino Web Agent. These settings determine how Domino authenticates and authorizes a user with CA SiteMinder®. You can configure these settings centrally in the Agent Configuration Object on the Policy Server or locally in the Agent configuration file on the web server.
Note: The Domino Web Agent does not support the auditing feature used to track user activity.
The Domino Directory is integrated with every Domino server. You can enable LDAP service for the Domino server so that Policy Server can use the Domino Directory to authenticate and authorize users. If you enable Domino’s LDAP service, you do not need to configure a separate user directory for authentication.
To enable LDAP service, see your Domino Server documentation.
Use the following guidelines when creating CA SiteMinder® policies for the Domino server:
For $defaultNav, the Domino Agent performs an action of ?OpenDatabase. You do not need to create additional rules for these types of identifiers.
The Domino server can represent the same Notes object in different ways. An object can be identified using the name, ReplicaID, UniversalID, and alias.
For the Domino Web Agent to communicate effectively with the Domino server, the Domino Agent processes access requests to Notes resources using only the object name. This enables the CA SiteMinder® policy store to understand the entry.
Expressed as a URL, the access method to any resource would be:
http://host/database.nsf/resource_name?Open
Actions for the Notes database resources should be considered when you create rules. Any resource not specified with an action will default to the action ?Open. The rules that are included in a CA SiteMinder® policy must account for the default action, ?Open, and equivalent actions for ?Open, such as ?OpenDatabase, ?OpenView, ?OpenDocument, ?OpenFrameset.
The Domino Web Agent enables a policy administrator to create one rule for many aliases that point to the same resource. You only need one rule because the Domino Agent converts Domino’s multiple representations of a resource into one URL. This function of the Domino Agent is important to consider when creating rules for CA SiteMinder® policies.
You create realms and rules using the Administrative UI.
Note: For more information, see the Policy Server documentation.
In the following illustration, the URL is a link to Acme’s Domino server, with a Notes database called db1.nsf. This database contains two files: page1 and page2.
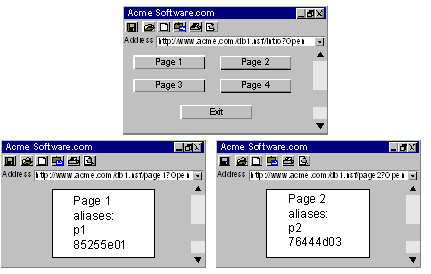
Example 1: Protecting one document and all its aliases.
For access to page1 and all its aliases, you create only one rule for the realm db1.nsf. The Domino Agent is able to interpret all the different naming conventions and convert them to a one standard URL format.
For your realms and rules, do the following:
Resource filter: /db1.nsf/
To protect not only page1 but all its aliases, you would configure the following:
Resource filter: /db1.nsf/page1
Resource: *
This * wildcard indicates that any action, such as ?Open, ?EditDocument can be performed on page1 by the users that are bound to the policy.
Example 2: Protecting different documents in the same database.
To protect page2 in the db1.nsf database in addition to page1, you need to create a second rule.
Resource Filter: /db1.nsf/page2
Resource: *
Example 3: Protecting different actions on a single resource
To protect individual actions on a resource, for example, if you wanted only some users to perform the action ?EditDocument and all users to perform the action ?ReadForm, each action would require its own rule for each resource, as follows:
Resource Filter: /db1.nsf/page1
Resource: ?OpenView
Resource Filter: /db1.nsf/page1
Resource: ?EditDocument
You could also use one rule as follows:
Resource Filter: /db1.nsf/page
Resource: ?Open*
Note: In the Resource field, there is no forward slash (/) before ?Open.
Even if there are aliases for this resource, the one rule would protect the original page and all its aliases.
Instead of creating several rules for different actions, you could specify a single rule and use wildcards to cover all actions, for example:
Resource filter: /db1.nsf/page
Resource: ?Open*
With the rule, you are then protecting the resource:
http://www.acme.com/db1.nsf/page*?Open*
Note: If you want a rule to be literal, write a regular expression.
The Domino server must authenticate and authorize users even if CA SiteMinder® has already gone through this process. CA SiteMinder® works with Domino’s authentication process by providing the Domino server with a user identity that is also configured in the Domino Directory, which is the list of users and their privileges. The Domino server uses this identity to authenticate and authorize the user for access to database resources.
Note: A user name must be resolved unambiguously, or else the Domino Agent denies the authentication request. This may require some adjustments in your user directory.
The Domino Web Agent identifies the user to the Domino server as one of the following:
To determine which identity the Domino Web Agent uses when communicating with the Domino server, you configure the following parameters:
Determines which name to pass to the domino server for server authentication.
Identifies a user who has access to all resources on the Domino server.
Identifies a user with default access to the Notes database, which means this person has general access privileges.
Note: You can configure the DominoSuperUser and DominoDefaultUser locally, in the Agent configuration file, or centrally, in the Agent Configuration Object. In the Agent configuration file, these settings have encrypted values. In the Agent Configuration Object, you have the choice of encrypting these values or leaving them in plain text.
A Domino Super User is a user who has access to all resources on the Domino server. If your Web site or portal is designed with CA SiteMinder® in mind, you are securing resources and applications by implementing CA SiteMinder® policies. As a result, the Domino server does not have to restrict user access based on its own security. In this case, users can be identified as the Super User for Domino’s authentication purposes.
To identify the user as the Super User, you enable the SkipDominoAuth parameter and specify a value for the DominoSuperUser parameter. This action makes sure that CA SiteMinder® and not Domino authenticates users. The user that you specify must also be in the Domino Directory.
If a user is defined in the Domino Directory, Domino authenticates that user with their user name. However, if the user is not in the Domino Directory, and they have been authenticated by CA SiteMinder® against another user directory, then the Domino Web Agent identifies that user to the Domino server as the DominoDefaultUser.
The default user has default access to the Notes database, which means this person should have general access privileges such as Domino’s depositor, reader, or author level of access, configured in ACLs.
For the Domino Agent to use this value, set the SkipDominoAuth parameter to no.
There may be some Notes databases that do not require protection from CA SiteMinder®. Resources that are not protected by CA SiteMinder® are not authenticated as the default Domino user. Instead, the Domino server prompts users for their credentials (if anonymous access is disabled).
To modify the DominoDefaultUser and DominoSuperUser parameters, do one of the following:
You can modify the DominoDefaultUser and DominoSuperUser settings in the Agent Configuration Object. You can choose whether the values are encrypted or in plain text.
Note: For more information, see the Policy Server documentation.
In the Agent configuration file, the DominoDefaultUser and DominoSuperUser values must be encrypted. Consequently, you have to modify these values using the encryptkey tool.
Important! Do not edit these settings directly in the Agent configuration file.
To set or change the value of DominoSuperUser or DominoDefaultUser in the Agent configuration file
/$HOME/ca/SiteMinder/Web Agent/bin
C:\Program Files\ca\SiteMinder Web Agent\Bin
encryptkey -path path_to_Agent_config_file
-dominoSuperUser new_value
encryptkey -path path_to_Agent_config_file
-dominoDefaultUser new_value
For example:
encryptkey -path "c:\program files\ca\SiteMinder Web Agent\Bin\Lotus Domino5\webagent.conf"
-dominoSuperUser admin
Note: The path to the Agent configuration file must contain the file name, such as, webagent.conf. Also, if any value in the path contains spaces, the entire path must be surrounded by quotation marks.
Note: The encryptkey tool is not provided as a part of the CA SiteMinder® Web Agent kit. However, the tool remains useful to Domino users who can manipulate it to generate encrypted DominoSuperUser settings for local configuration. You can contact Support to download a copy of this tool.
To have CA SiteMinder® (and not Domino) authenticate users, set the SkipDominoAuth parameter to yes.
With SkipDominoAuth set to yes and a Super User defined, CA SiteMinder® first identifies and authorizes the user. The Domino Web Agent then identifies that user to the Domino Server as the Super User. As a Super User, the user has access to any resource on the Domino server, assuming the user has the appropriate ACLs.
You should also set SkipDominoAuth parameter to yes when users are not stored in the Domino Directory because Domino will not have an identity to use for authorization privileges.
If you set SkipDominoAuth to no, Domino authenticates users on its own using the actual user name or the default user name.
The following table shows how the setting of the SkipDominoAuth parameter affects how the user is identified.
|
SkipDominoAuth Value |
Identified to the Domino Server As |
Notes |
|---|---|---|
|
yes |
Super User |
Super User must be defined in the Domino Directory |
|
no |
Actual User |
User must be in the Domino Directory |
|
no |
Default User |
User must be in the Domino Directory |
|
no |
Super User |
The requested resource is automatically authorized, meaning that no authentication challenge will be presented to the user |
The DominoUseHeaderForLogin and DominoLookUpHeaderForLogin parameters can be used to identify a Domino user for authentication.
Instructs the Domino Web Agent to pass the CA SiteMinder® header value to the Domino Web Server. The Domino server uses the header data to identify a user in its user directory.
Set this parameter to a header name. For example, if you specify DominoUseHeaderForLogin="HTTP_SM_USER", the Web Agent passes the user’s login name to the Domino server.
Instructs the Domino Web Agent to ask the Domino Web Server if the user requesting access to a resource is unique or ambiguous within the Domino user directory. This check is useful if a user named Jones tries accessing a resource and there are several users named Jones in the user directory. If this parameter is set to no, the Domino Web Agent does no checking with the Domino Web Server.
Default: Yes
CA SiteMinder® provides authentication and authorization functionality; therefore, the Domino session authentication feature is not needed. It should be disabled if the Web Agent is installed.
Under some conditions, having Domino session authentication enabled causes the user session to behave differently. This change in behavior does not affect security on a CA SiteMinder®-enabled site. It reflects the intersection of CA SiteMinder® and Domino session management rules.
To use an anonymous CA SiteMinder® authentication scheme with a Domino agent, set the following parameter:
Specifies a value for anonymous users. This value is sent to the Domino server when users access Domino resources that are protected with an anonymous CA SiteMinder® authentication scheme.
Default: No (anonymous authentication scheme not used)
Example: Anonymous (use with anonymous authentication schemes)
The previous parameter applies only when using an anonymous CA SiteMinder® authentication scheme with Domino. Do not change its value for other authentication schemes or server types.
A credential collector is an application within the Web Agent, which gathers user credentials for forms, SSL, and Windows authentication schemes, and for single sign-on across multiple cookie domains. The credentials gathered by the credential collector are based on the type of authentication scheme configured for a particular group of protected resources.
For a Domino Web Agent to act as a credential collector, you have to configure various MIME types, represented as file extensions in the Agent configuration file.
Credential collectors are generally auto-authorized, that is, when you add a file extension to these parameters, they are, by default, included in the IgnoreExt parameter. Domino Server cannot correctly process URLs that include files with these extensions, so the Domino Agent has to ignore these files.
Note: For more information, see the Policy Server documentation.
|
Copyright © 2014 CA.
All rights reserved.
|
|