

Authentication schemes provide a way to collect a user’s credentials and determine the user’s identity.
The Policy Server includes a variety of standard authentication schemes. These schemes range from basic user name/password authentication and HTML forms-based authentication to digital certificate and token authentication.
If the standard authentication schemes included with the Policy Server do not provide the kind of authentication functionality required at your site, you can use the Java Authentication API to create a custom authentication scheme.
The base interface in the Java Authentication API is SmAuthScheme. All custom authentication schemes created with the Java Authentication API must implement this interface.
SiteMinder calls the following methods in the base interface SmAuthScheme:
|
Method |
Description |
|---|---|
|
authenticate() |
Performs the custom authentication and returns the authentication result. SiteMinder calls this method at least twice—to establish user context and to authenticate the user’s credentials. |
|
init() |
Performs any initialization procedures that the authentication scheme requires. SiteMinder calls this method once for each authentication scheme instance, when the authentication scheme is loaded. |
|
query() |
Provides SiteMinder with either of the following kinds of information, depending on the value SiteMinder passes in the reason parameter (object SmAuthQueryCode): The version and description of the authentication scheme. The kind of credentials that SiteMinder should collect from the user, and optionally, the URL for the site where credentials should be collected. |
|
release() |
Performs any rundown procedures that the authentication scheme requires. SiteMinder calls this method once for each authentication scheme instance, when SiteMinder is shutting down. |
The following classes are used in conjunction with the SmAuthScheme base interface:
|
Class |
Description |
|---|---|
|
SmAuthenticationContext |
Contains the following context classes passed to authenticate(): APIContext UserContext UserCredentialsContext The set... methods in this object pass information directly to SiteMinder. |
|
SmAuthenticationResult |
Contains status and reason codes returned to SiteMinder after a call to authenticate(). |
|
SmAuthQueryCode |
Contains the type of request that SiteMinder is making of the authentication scheme (version number and description, or information about the credentials that SiteMinder must collect). SiteMinder passes this object to the authentication scheme in query(). |
|
SmAuthQueryResponse |
Contains constants that specify the kind of credentials that are required for authentication, if any. Also allows a text message to be returned to SiteMinder for display to the user. Optionally, the authentication scheme can call setResponseBuffer() to specify a URL where credentials must be collected. The set... methods in this object pass information directly to SiteMinder. |
|
SmAuthStatus |
Contains Authentication API status codes such as SMAUTH_ACCEPT and SMAUTH_REJECT. This object can be passed back to SiteMinder in SmAuthenticationResult. It is also the return value type for the authentication scheme’s init(), query(), and release() methods. |
|
UserCredentialsContext |
Contains credentials information and other information from the user directory where user context was established. This object is contained in the SmAuthenticationContext object passed to authenticate(). |
When user authentication is to occur against a custom authentication scheme created with the Java API, SiteMinder loads the custom scheme by loading:
Immediately after the scheme is loaded, SiteMinder calls the following methods in the custom class implemented from SmAuthScheme:
Note: When SiteMinder passes SMAUTH_QUERY_CREDENTIALS_REQ in query(), SiteMinder is requesting that the authentication scheme specify the kind of credentials that are required. SiteMinder then collects the specified credentials.
The following figure shows the key activities that occur during authentication:
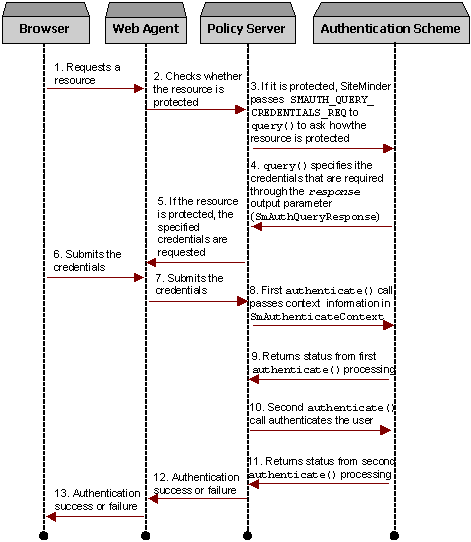
The Java Authentication API supports authentication based on the following general types of credentials requirements:
You specify the authentication credentials that are required through the setResponseBuffer() method in the object SmAuthQueryResponse. This object contains a number of constants that indicate the specific credentials that are required or whether no credentials are required.
The authentication process includes two phases—user disambiguation and user authentication.
Before a user can be authenticated, the user’s profile information must be retrieved from the user store so that the user’s stored credentials can be compared with the credentials supplied at login. Looking up the user in a user store (such as an LDAP user directory or an ODBC database) is called user disambiguation. Either SiteMinder or the authentication scheme can disambiguate the user.
SiteMinder calls SmAuthScheme.authenticate() at least once during the disambiguation phase and at least once during the authentication phase:
The basic steps are as follows:
uid=jsmith,ou=marketing,o=myorg.org
An LDAP search expression can also be used to search an LDAP user directory, and a SQL query is used to search an ODBC database—for example:
(&(objectclass=inetOrgPerson)(uid=jsmith))
select Name from SmUser where Name = 'jsmith'
Multiple results are possible, given that the LDAP DN or the ID stored in the ODBC database might apply to different users who have different passwords.
SiteMinder first calls authenticate() at the beginning of the user disambiguation phase.
Either SiteMinder or the custom authentication scheme can disambiguate the user. The authentication scheme indicates whether it has performed the disambiguation through a combination of the following:
The status codes are set in the SmAuthStatus object. This object is passed in the status parameter of the SmAuthenticationResult constructor. SmAuthenticationResult is returned from authenticate():
The authentication scheme asks SiteMinder to disambiguate the user.
When returning this status code, the authentication scheme should also return an empty string through the setUserText() method. SiteMinder gets the login ID from the Agent, constructs the DN or search expression based on the login ID and the information defined in the SiteMinder User Directory Properties dialog box, and disambiguates the user by looking up the user in the user store.
The authentication scheme asks SiteMinder to disambiguate the user.
The authentication scheme passes the login ID to SiteMinder through setUserText(). SiteMinder uses that value to construct the DN or search expression and disambiguate the user in the user store. This approach gives the authentication scheme the opportunity to modify the login ID before SiteMinder disambiguates the user.
Note: If the authentication scheme passes an empty string in setUserText(), SiteMinder uses the login ID provided by the Agent (the same behavior as with return code SMAUTH_NO_USER_CONTEXT).
The authentication scheme disambiguates the user by constructing the complete DN or search expression and looking up the user in the user store. The authentication scheme passes the user’s complete DN or ODBC database ID to SiteMinder in setUserText(). Only one DN or database ID can be passed in setUserText().
The user cannot be found in the directory.
This is returned if an error condition exists. Error text is returned to SiteMinder through the setUserText() method.
During this phase, SiteMinder calls authenticate() again to allow the authentication scheme to verify the supplied credentials after the user context has been established during disambiguation. The method sets one of the following status codes:
Your authentication scheme can have the Policy Server instruct the agent to perform a redirect. To build redirection capabilities into your authentication scheme:
SmAuthenticationContext.setErrorText()
Authentication results are tied to SiteMinder events. If authentication events are enabled in the realm where the user is being authenticated, SiteMinder evaluates optional policies tied to OnAuthAccept, OnAuthReject, OnAuthAttempt, and OnAuthChallenge rules. You can configure these policies to return custom responses based on a user’s identity, redirect the user to another location based on the result of the authentication, or update the user data in an external database.
|
Copyright © 2015 CA Technologies.
All rights reserved.
|
|