

To use the Credentials Selector, configure the protected realms of a CA SiteMinder® application with the front-end authentication scheme of the component. The policies protecting the application can have restrictions that are based on the user authentication level and authentication context.
In this solution, the sample application generates the greeting message for the authenticated and authorized user.
The file that generates this greeting has the following code:
<html>
<head></head>
<body>
<h3>
<p>Greetings, <%=Request.ServerVariables("HTTP_USERNAME") %>!
<p>Your authentication level is <%=Request.ServerVariables("HTTP_AUTHLEVEL") %>
<p>You have used <%=Request.ServerVariables("HTTP_AUTHCONTEXT") %> authentication
</h3>
</body>
</html>
The different authentication options in the login dialog result in different access levels and a different greeting, such as:
Greetings, SampleUser! Your authentication level is 5 You have used username/password authentication
Greetings, SampleUser! Your authentication level is 10. You have used X.509 client certificate authentication
Greetings, SampleUser! Your authentication level is 5 You have used Windows domain authentication
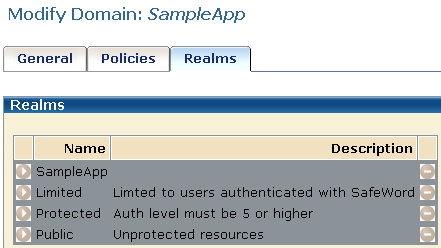
The sample application has four kinds of resources that are contained in different realms. The realms must each be configured with the front-end authentication scheme.
For this example, the following four realms protect the various resources that make up the sample application:
The realms are shown in the following illustration.
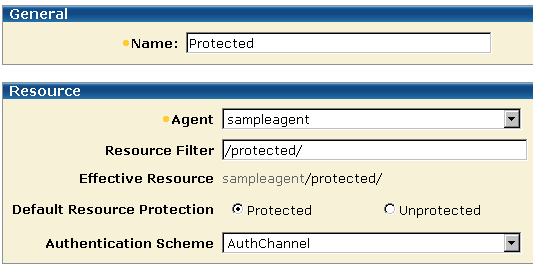
The protected realms are configured with the AuthChannel front-end authentication scheme, as shown in the following illustration.
The SampleAgentGroup can contain any Web Agents that provide points of entry to the sample application.
The following requirements are necessary for agents that are protecting realms as part of the Credentials Selector functionality:
The expected value is the value of the AgentName parameter or the DefaultAgentName parameter, if the AgentName parameter is not assigned a value. If the EncryptAgentName parameter in the agent configuration is set to yes, the value must be encrypted.
One way of setting the @smagentname directive is by configuring each Web Agent with the same naming properties. They can even share an Agent Configuration Object. Another method is to configure the @smagentname directive programmatically in the FCC file, if the name is not encrypted.
Important! If the @smagentname directive is misconfigured, you can see a “No realm received in request” error message in the Policy Server log.
You can configure any type of rule for the realms that contain the sample application resources.
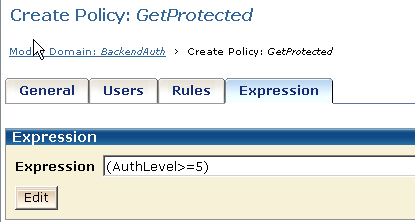
The GetProtected policy requires a protection level of 5 or greater for access to protected resources. To enforce this protection level restriction, you can write an active expression in the GetProtected policy to retrieve the SM_AUTHENTICATIONLEVEL attribute from the CA SiteMinder® session ticket.
Note: This authentication level restriction is designed to protect applications from custom Web Agents that only support password authentication levels of one.
When legacy federation is in use, you can create a user context variable that is named AuthLevel and can use it in the GetProtected policy to define an active expression that retrieves the SM_AUTHENTICATIONLEVEL attribute from the session ticket.
In this example, the sample application that displays the greeting message uses three HTTP header variables:
These headers are returned to the client with the following response:
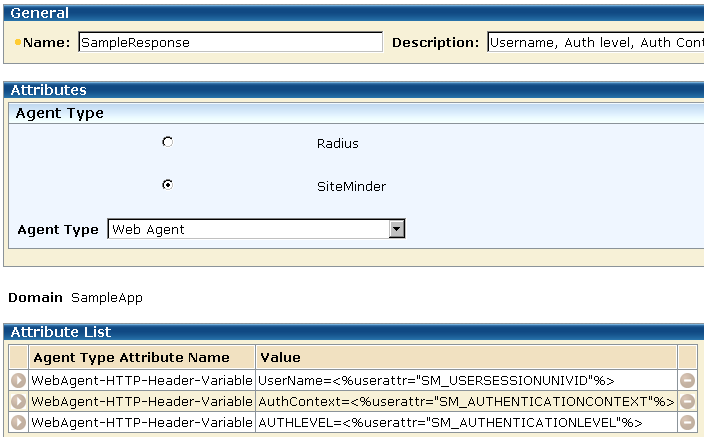
Attribute values are specified on the Response Attribute pane.
|
Copyright © 2015 CA Technologies.
All rights reserved.
|
|