

Policy Server Guides › Policy Server Configuration Guide › Using the Policy Server as a RADIUS Server › How to Authenticate Users in Heterogeneous RADIUS Environments with Two User Directories
How to Authenticate Users in Heterogeneous RADIUS Environments with Two User Directories
The Policy Server can also be configured to authenticate users for multiple NAS devices when the user information for each device is located in separate user directories. The NAS devices can be of different vendor types.
There are several advantages to this configuration:
- Using two user directories in a single policy domain enables you to delegate the administration of each directory to a different person.
- By configuring the Policy Server to authenticate users for multiple RADIUS clients, you save time. You do not need to install and configure a separate authentication server for each RADIUS client.
- Using existing user directories is more efficient. You do not need to merge the user information into a single directory.
An example of a heterogeneous configuration that uses two user directories is illustrated in the following graphic:
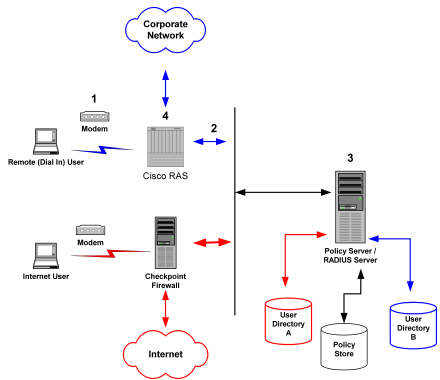
Unlike the topology described in the previous section, this Policy Server uses two user directories to authenticate the users. User information for the Cisco RAS users is stored in User Directory A. User information for the Checkpoint firewall is stored in User Directory B. The Policy Server can authenticate users using both of these directories.
By dividing the configuration into two policy domains, the need for realm hints is eliminated. Each RADIUS Agent exists in a separate policy domain and is bound to only one realm.
The process of authentication when two user directories are used is as follows:
- The remote user dials in from a modem and the Cisco RAS determines that it must use a RADIUS user profile to authenticate the user.
- The RAS sends the user connection request to the Policy Server.
- The Policy Server enacts the policy defined for the RAS, and the RADIUS Agent obtains the user’s name and password using the authentication scheme configured for the Agent.
- The Policy Server evaluates the user information against the user directory and policy store associated with the policy’s domain.
- The Policy Server sends an authentication response to the Cisco RAS and one of the following takes place:
When the Internet user attempts to dial into the Internet Service Provider by using the Checkpoint Firewall, this same process of authentication occurs. However, the Policy Server evaluates the Internet user’s authentication information against a different user directory.
How to Configure the System and Policy Domain
To configure the heterogeneous environment described above, which includes two user directories, you must:
- Configure the system:
- Define two RADIUS Agents, as described in Define Agents for a Heterogeneous, Two Directory Environment.
- Set up the user directories, as described in Set Up User Directories.
- Create two policy domains, as described in Create Two Policy Domains.
- Configure the policy domain:
- Define one realm. The realm binds a RADIUS Agent with a RADIUS authentication scheme.
- Define a rule that enables authenticated users to access the realm. Each rule binds a realm with an allow or deny access event.
- Define a response that provides the user profile to the NAS device and optionally, configures the characteristics of the session using response attributes.
- Create a policy that binds the rule with the response. This policy also binds the rule and response with the RADIUS user directory.
A diagram of these two policy domains is shown in the following graphic:
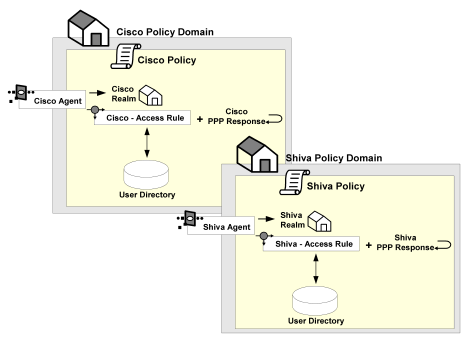
Define Agents for a Heterogeneous Two Directory Environment
For this environment, you must configure two RADIUS Agents:
- One Agent must be associated with the Cisco RAS.
- One Agent must be associated with the Checkpoint Firewall.
- Neither RADIUS Agent requires a realm hint.
More information:
Define Agents for a Heterogeneous, Single Directory Environment
Set Up User Directories
Each of the user directories containing RADIUS user information must be configured in the Policy Server. Each directory will be associated with a separate policy domain so that separate administrators can be defined for each policy domain.
Create Two Policy Domains
One policy domain must be created for the Cisco RAS and one policy domain must be created for the Checkpoint firewall. When defining the policy domains, associate each domain with the appropriate user directory.
Copyright © 2015 CA Technologies.
All rights reserved.
 
|
|



