

The legacy federation or partnership federation model can establish a federated partnership between Financepro and BankLtd. Using federation, users move between each company as if they are one company.
Configure the partnership model in the Administrative UI, guided by a partnership wizard. The partnership objects focus on creating partnerships and identifying each side of the partnership to accomplish single sign-on.
These steps in the partnership wizard include:
Names the partnership and identifies the two entities that make up the partnership.
Identifies the users for which the asserting party generates assertions/tokens and the relying party authenticates.
Determines how a federated identity is established and lets you add attributes to identify and customize the content of the assertion.
Using the NameID and attributes, you can verify that the appropriate information is available to the application at the relying party. The NameID and Attributes step is where you configure account linking and identity mapping.
Defines the Single Sign-on binding, including the location of the service consuming assertions at the relying party. For SAML 2.0, you can configure more features, such as single logout (SLO), authentication context, Enhanced Client or Proxy (ECP) profile, and Identity Provider Discovery profile. For WS-Federation, you can configure sign-out.
Enables the Service Provider to obtain information about the authentication process to establish a level of confidence. This feature also enables the Identity Provider to include the authentication context in an assertion.
Defines the signature and encryption options for secure exchange of data, including:
Enables you to configure redirection to the target application, lets you set up provisioning of user records, and define relying-party side attribute mapping. You can also set up redirects for failed user authentication.
The legacy federation model focuses on the domain, realm, rule, authentication schemes, and policy objects.
If CA SiteMinder® is the asserting party, the configuration steps include:
Names the partner for which the asserting party generates assertions.
Specifies the user directories for which the asserting party generates assertions and the relying party authenticates.
Determines how a federated identity is established. In the profiles configuration, you add attributes to identify and customize the content of the assertion.
Using NameID and attributes, you can verify that the appropriate information is available to the application at the relying party. The profiles configuration is where you specify account linking and identity mapping.
As part of the profiles, configure single sign-on. For SAML 2.0, you can configure more features, such as single logout (SLO), Enhanced Client or Proxy (ECP) profile, and Identity Provider Discovery profile. For WS-Federation, you can configure sign-out.
Defines the signature options for secure exchange of assertions, authentication requests, and single logout requests and responses.
If CA SiteMinder® is the relying party, the configuration steps include:
Enables you to configure redirection to the target application, lets you set up provisioning of user records, and define relying-party side attribute mapping.
Configure the components to establish successful federated partnerships. Most of these components are configurable using the Administrative UI.
The following flow chart highlights the general process for legacy federation and partnership federation.
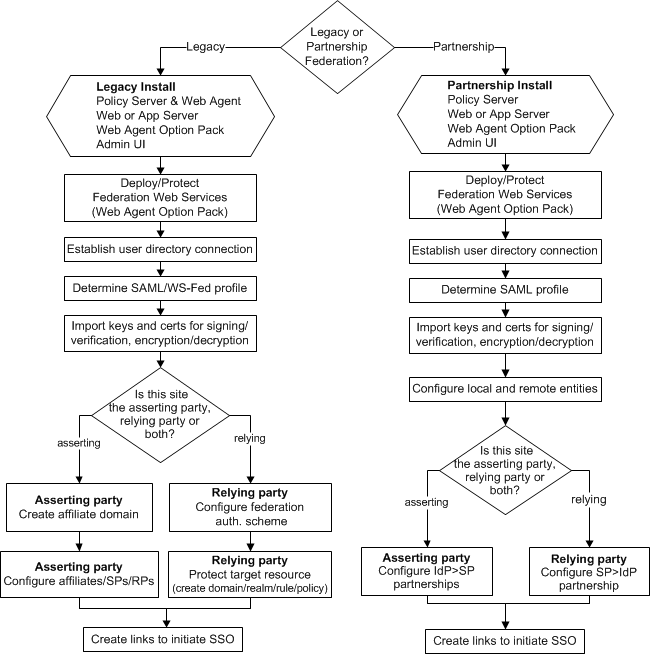
See the following guides for detailed instructions on required components and configuration procedures:
Partnership Federation Guide
Partnership Federation refers to partnership model of federation.
Legacy Federation Guide
Legacy federation refers to the product known as Federation Security Services
|
Copyright © 2015 CA Technologies.
All rights reserved.
|
|