

What is the peak request rate for the web service?
The peak request rate is based on the sustained request rate, specifically, when and at what rate the system is operating at peak levels. Estimating the peak request rate is the process of identifying when the system is servicing the highest level of requests.
When estimating the peak request rate, we recommend that you use the metrics you gathered when determining the sustained request rate to determine:
The following figure is an example of these metrics:
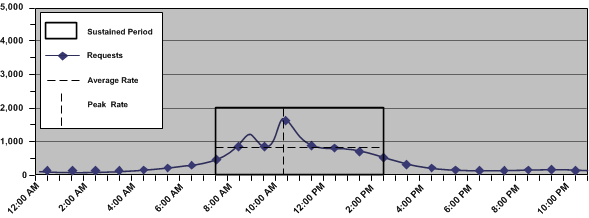
Identifying these metrics helps you to estimate the number of requests, per second, that CA SiteMinder® must service to maintain the peak rate at which web service clients authenticate, which the following represents:
(request_load x percentage_of_transactions) / number_of_hours / 3600 = peak_request_rate
Note: This rate is based on the single busiest hour. There can be periods when the peak request rate exceeds the hourly calculation.
Represents the number of daily requests for the web service.
Represents the percentage of transactions that occur when the system is operating at peak levels.
Represents the number of hours in which the system operates at peak levels.
Note: 3,600 represents the number of seconds in an hour.
Represents the peak request rate for the application.
Example: Estimate the Peak Request Rate
The company has determined that their web service has a daily request load of 8,800. System activity reports detail that during the single busiest hour of the day 1,800 requests occur. This number represents approximately 20 percent of the request load:
1,800 / 1 / 3600 = 0.5 requests per second
The fulfillment web service has a peak request rate of five requests per second.
Note: This example is based on the single busiest hour. There can be periods when the peak request rate during the hour exceeds five requests per second.
Although request rates are the most significant factors in CA SiteMinder WSS capacity planning decisions other factors can also influence CA SiteMinder® performance, in particular the authentication schemes used to protect your web services.
Also consider performance tuning and network bandwidth in your capacity planning process.
|
Copyright © 2015 CA Technologies.
All rights reserved.
|
|