

The following process lists the steps for configuring a CA LDAP Server for z/OS user store connection to the Policy Server:
You can configure a CA LDAP Server for z/OS as a user store by configuring a connection from the Policy Server to the LDAP Server. How you configure the connection from the Policy Server to the LDAP Server depends on the backend option that you are using to secure the LDAP Server:
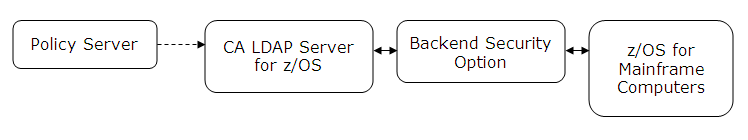
CA supports the following backend security options for CA LDAP Server:
Become familiar with the objectclass hierarchy for these backend security options before configuring the connection from the Policy Server to the LDAP Server. Also, add the backend-related objectclasses to the Policy Server registries in the LDAP namespace.
Note: z/OS is an IBM operating system for mainframe computers.
CA LDAP Server for z/OS does not support the following features:
Password Services is not supported.
When configuring a CA LDAP Server r15 for z/OS as a user store, provide values for the Administrator Credentials in the Create User Directory page.
The following characters are not supported in user names:
Adding a user group to a policy and attempting to authorize a user in that group fails.
Load balancing and failover is not supported.
LDAP Failover and Replication is not supported.
When you are using TSS to secure the CA LDAP Server for z/OS, complete the following steps before configuring the connection from the Policy Server to the CA LDAP Server:
The following diagram shows the hierarchy of objectclass entries in the CA Top Secret Directory Information Tree (DIT). Below the diagram is a description of each objectclass.
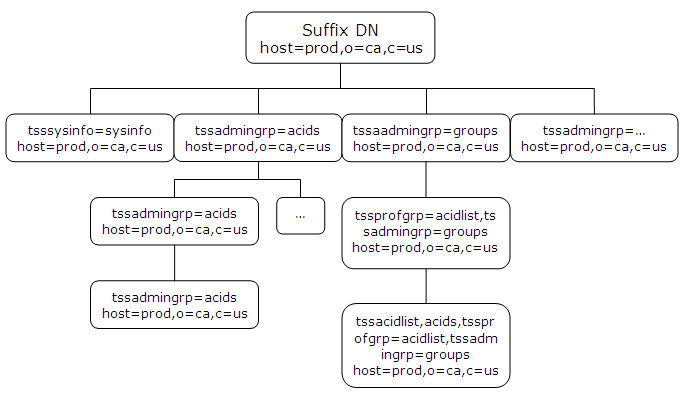
Object class used to start access to the objectclass hierarchy for a CA Top Secret database.
Object class used to create branches in the objectclass hierarchy below the host.
Object class used to create branches in the objectclass hierarchy below the host.
Values:
Object class used to access the ACID record fields of all user types.
Object class used to create the branches in the objectclass hierarchy below an acid.
The CA LDAP Server for z/OS contains different object classes than other LDAP servers. Before configuring a connection from the Policy Server to the CA LDAP Server, add the TSS objectclasses to certain Policy Server registry entries in the LDAP namespace. Substitute the replacement values for the default values of the following Policy Server registry entries:
Specifies the following registry entry location:
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Netegrity\SiteMinder\CurrentVersion\Ds.
Specifies the default value of the registry entry.
Specifies a new value containing the TSS objectclasses for the registry entry.
organization,organizationalUnit,groupOfNames,groupOfUniqueNames,group
class_filters_default_value,eTTSSAcidName,tssacidgrp,tssadmingrp
groupOfNames,groupOfUniqueNames,group
group_class_filters_default_value,eTTSSAcidName,tssacidgrp,tssadmingrp
organizationalPerson,inetOrgPerson,organization,organizationalUnit, groupOfNames,groupOfUniqueNames,group
policy_class_filters_default_value,eTTSSAcidName,tssacidgrp,tssadmingrp
Add the following TSS object classes to this registry entry:
|
TSS Objectclass |
Registry Key Type |
Data |
|
eTTSSAcidName |
REG_DWORD |
0x00000001(1) |
|
tssacid |
REG_DWORD |
0x00000001(1) |
|
tssacidgrp |
REG_DWORD |
0x00000002(2) |
|
tssadmingrp |
REG_DWORD |
0x00000003(3) |
Note: Some LDAP queries that the Policy Server issues (such as a full list of users) can take up to 60 seconds to complete. Under these conditions most of the queries from the Policy Server-side timeout. To improve connectivity, you can adjust this registry key entry as follows:
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Netegrity\SiteMinder\CurrentVersion\Debug]
LDAPPingTimeout = 300; REG_DWORD
You configure the user directory connection to let the Policy Server communicate with the user store.
Note: Load balancing and failover are not supported for this LDAP server.
Follow these steps:
Note: Be sure to enter 100 in Max Time. The Policy Server requires this amount of time to retrieve data from this LDAP Server.
Note: TSS does not allow anonymous binds to the user store.
The user directory connection is created.
This section describes the settings that are required to configure the CA LDAP Server r15 for z/OS (ACF2) as a user store with the Policy Server.
The following illustration shows the hierarchy of objectclass entries in the CA ACF2 Directory Information Tree (DIT). The illustration provides a description of each objectclass.
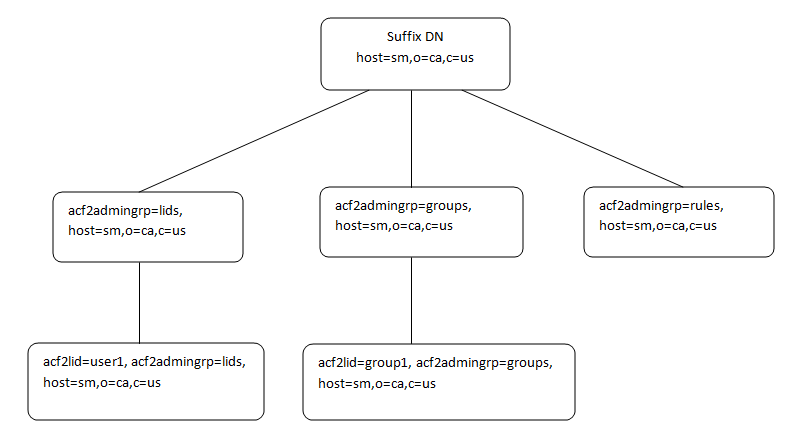
Object class that is used to start access to the objectclass hierarchy for a CA ACF2 database.
Object class that is used to create branches in the objectclass hierarchy below the host.
Object class that is used to access the LID record fields (user records). The acf2lid is the only objectclass that can be added, modified, and deleted. All other objectclass objects are read-only.
Object class that is used to emulate groups in CA ACF2.
Object class that is used to group like rule types. The acf2ruletype objectclass is read-only and cannot be modified, added, or deleted.
The CA LDAP Server r15 for z/OS (ACF2) contains a different set of objectclasses than other LDAP servers. Before configuring a user directory connection from the Policy Server to the CA LDAP Server, add the ACF2 objectclasses to certain Policy Server registry entries in the LDAP namespace. Substitute the replacement values for the default values of the following Policy Server registry entries:
Specifies the following registry entry location:
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Netegrity\SiteMinder\CurrentVersion\Ds.
Specifies the default value of the registry entry.
Specifies a new value containing the ACF2 objectclasses for the registry entry.
organization,organizationalUnit,groupOfNames,groupOfUniqueNames,group
class_filters_default_value,*
groupOfNames,groupOfUniqueNames,group
group_class_filters_default_value,*
organizationalPerson,inetOrgPerson,organization,organizationalUnit,groupOfNames,groupOfUniqueNames,group
policy_class_filters_default_value,*
Add the following ACF2 objectclasses to this registry entry:
|
ACF2 Objectclass |
Registry Key Type |
Data |
|---|---|---|
|
acf2lid |
REG_DWORD |
0x00000001(1) |
|
acf2admingrp |
REG_DWORD |
0x00000002(2) |
|
eTACFLidName |
REG_DWORD |
0x00000001(1) |
In UNIX, add the following ACF2 objectclass to this registry entry:
|
ACF2 Objectclass |
Registry Key Type |
Data |
|---|---|---|
|
LDAPPingTimeout= |
REG_DWORD |
300; |
Note: The value of this registry key can be changed based on the response time of the CA LDAP Server r15 for z/OS (ACF2).
This section describes the settings that are required to configure the CA LDAP Server r15 for z/OS (RACF) as a user store with the Policy Server.
The following illustration shows the hierarchy of namespace entries in the RACF Directory Information Tree (DIT). The illustration provides a description of each namespace. The RACF namespace hierarchy is similar to the ACF2 object class hierarchy.
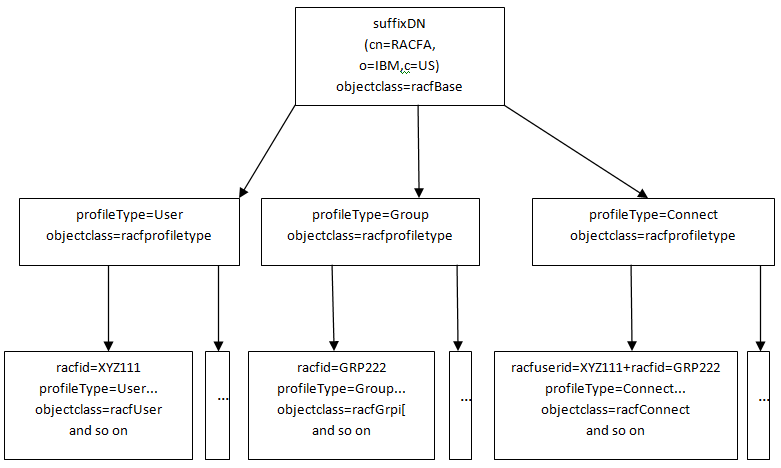
Similar to the ACF2 Server, the top four entries in the hierarchy are reserved, read-only, and generated by the server. The purpose of these reserved entries is to enable a hierarchical representation of RACF users, groups, and connections.
The CA LDAP Server r15 for z/OS (RACF) contains a different set of objectclasses than other LDAP servers. Before configuring a user directory connection from the Policy Server to the CA LDAP Server, add the RACF objectclasses to certain Policy Server registry entries in the LDAP namespace. Substitute the replacement values for the default values of the following Policy Server registry entries:
Specifies the following registry entry location:
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Netegrity\SiteMinder\CurrentVersion\Ds.
Specifies the default value of the registry entry.
Specifies a new value containing the RACF objectclasses for the registry entry.
organization,organizationalUnit,groupOfNames,groupOfUniqueNames,group
class_filters_default_value,*
groupOfNames,groupOfUniqueNames,group
group_class_filters_default_value,*
organizationalPerson,inetOrgPerson,organization,organizationalUnit,groupOfNames,groupOfUniqueNames,group
policy_class_filters_default_value,*
Add the following RACF objectclasses to this registry entry:
|
RACF Objectclass |
Registry Key Type |
Data |
|---|---|---|
|
eTRACUserid |
REG_DWORD |
0x00000001(1) |
|
eTRACAdminGrp |
REG_DWORD |
0x00000002(2) |
In UNIX, add the following RACF objectclass to this registry entry:
|
RACF Objectclass |
Registry Key Type |
Data |
|---|---|---|
|
LDAPPingTimeout= |
REG_DWORD |
300; |
Note: The value of this registry key can be changed based on the response time of the CA LDAP Server r15 for z/OS (RACF).
To configure a directory connection from the Policy Server to the CA LDAP Server for z/OS (RACF) or CA LDAP Server for z/OS (ACF2), open an existing user directory object in the Administrative UI.
Follow these steps:
Note: Failover is not supported for this LDAP Server.
Note: A greater timeout value is required, because the Policy Server takes more time to retrieve data from this LDAP Server.
Important! Specifying administrator credentials is mandatory as anonymous binds to the user store are not allowed with CA LDAP Server r15 for z/OS (RACF) and CA LDAP Server r15 for z/OS (ACF2).
|
Copyright © 2015 CA Technologies.
All rights reserved.
|
|