

The CA SiteMinder® policy store is the repository for all policy–related information. All Policy Servers in a CA SiteMinder® installation must share policy store data, either directly or through replication. CA SiteMinder® is installed with tools that let administrators move policy store data from one storage facility to another.
When you install the Policy Server, you can automatically configure one of the following directory servers as a policy store:
If you do not use the Policy Server to configure a policy store automatically, you can manually configure a policy store after installing the Policy Server. Additionally, after you install the Policy Server, you can use the Policy Server Management Console to point the Policy Server to an existing policy store.
Note: For a list of supported CA and third-party components, refer to the CA SiteMinder® 12.51 Platform Support Matrix on the Technical Support site.
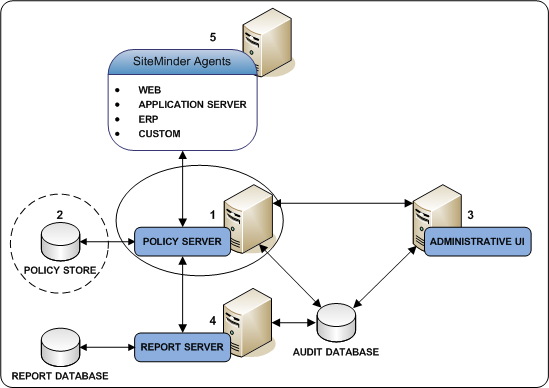
The following diagram illustrates a sample CA SiteMinder® installation and lists the order in which you install and configure each component.
The following figure depicts a single policy/key store instance. Although not illustrated, your environment can use separate instances for individual policy and key stores.
To avoid possible policy store corruption, ensure that the server on which the policy store will reside is configured to store objects in UTF-8 form. For more information on configuring your server to store objects in UTF-8 form, see the documentation for that server.
When you configure a policy store, the following default policy store object files are available:
Both files contain the default objects that the policy store requires.
Both files provide default security settings. These settings are available in the default Agent Configuration Object (ACO) templates that are available in the Administrative UI. The smpolicy-secure file provides more restrictive default security settings. Choosing smpolicy.xml does not limit you from using the more restrictive default security settings. You can modify the default ACO settings using the Administrative UI.
The following table summarizes the security settings for both files:
|
Parameter Name |
smpolicy Values |
smpolicy–secure Values |
|---|---|---|
|
BadCssChars |
No value |
<, >, ', ;, ), (, &, +, %00 |
|
BadQueryChars |
No value |
<, >, ', ;, ), (, &, +, %00 |
|
BadUrlChars |
//, ./, /., /*, *., ~, \, %00-%1f, %7f-%ff, %25 |
smpolicy.smdif values plus: <, >, ', ;, ), (, &, + |
|
EnableCookieProvider |
Yes |
No |
|
IgnoreExt |
.class, .gif, .jpg, .jpeg, .png, .fcc, .scc, .sfcc, .ccc, .ntc |
All smpolicy values. |
|
LimitCookieProvider |
No |
Yes |
|
ValidTargetDomain |
This file does not include this parameter. |
This parameter does not have a default value. Provide a valid redirection domain. Example: validtargetdomain=".example.com" |
|
Copyright © 2015 CA Technologies.
All rights reserved.
|
|