

Web Agent Guides › Web Agent Configuration Guide › Forms Authentication
Forms Authentication
This section contains the following topics:
How Credential Collectors Process Requests
MIME Types for Credential Collectors
How to Configure Basic FCC Authentication
Tune the Performance of the FCC
Specify an NTLM Credential Collector
Map URLs for FCC Redirects with a Domino Web Agent
Configure POST Preservation
Using Credential Collectors Between 4.x Type and Newer Type Agents
Configure Advanced FCC Settings
How Credential Collectors Process Requests
The following illustration describes how forms credential collectors (FCCs) process requests for protected resources:
Note: Cookie providers use a different process for single-sign on.
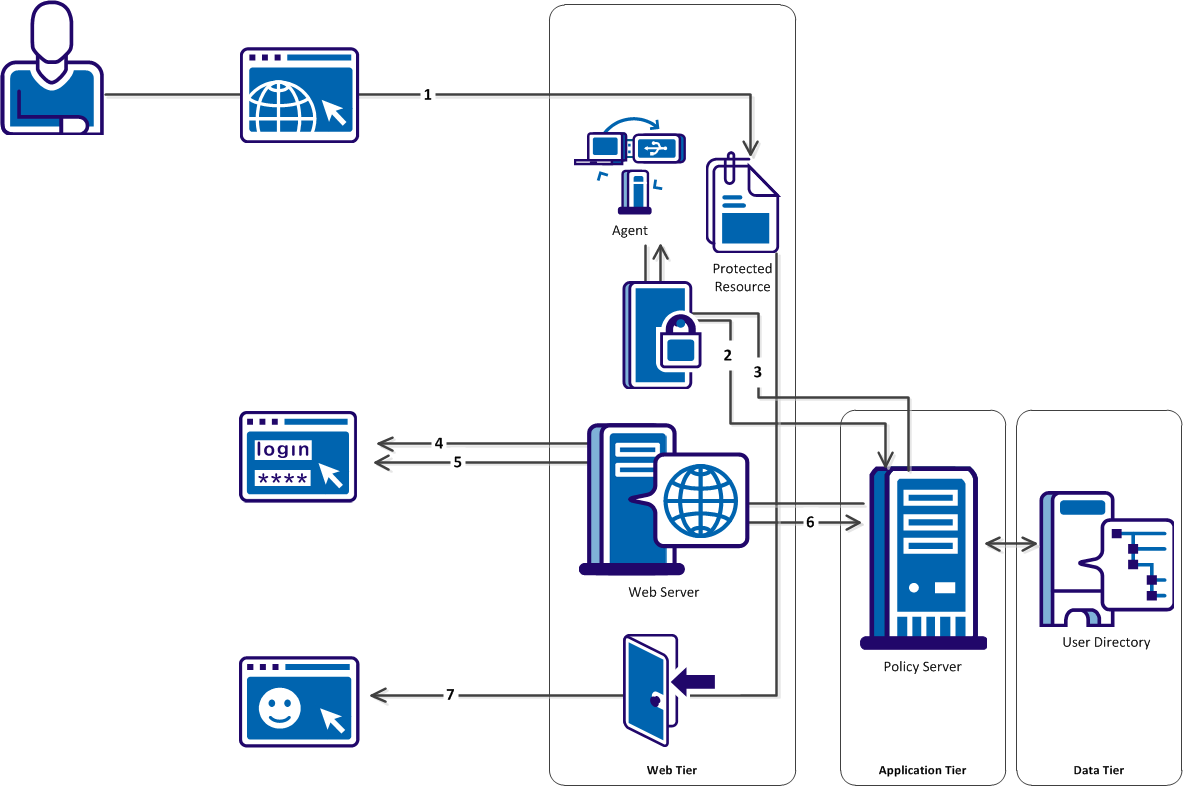
The process shown in the previous illustration describes the following steps:
- A user requests access to a resource.
- The agent contacts the Policy Server to determine whether the resource is protected.
- The Policy Server informs the agent that a credential collector protects the resource, and specifies the type of credential collector in use.
- The agent adds query data, the target resource and an encrypted agent name to the URL of the credential collector. The agent then redirects the user to the appropriate credential collector.
- One of the following actions occurs, depending on the type of credential collector:
- The FCC displays the form and then collects the credentials of the user.
- The NTC collects the NT credentials of the user.
- The SCC collects the credentials of the user.
- If no certificate is available, the SFCC displays the form. The SFCC collects the user credentials.
- The credential collector logs the user directly in to the Policy Server. The Policy Server creates a session.
- The agent validates the session and grants the user access to the resource.
Note: For more information about SSL Authentication Schemes, see the Policy Server documentation.
Copyright © 2012 CA Technologies.
All rights reserved.
 
|
|


