Your external security package can provide resource-level security if it supports SAF. It can provide security on its own or in conjunction with NPF.
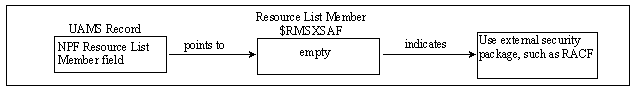
SAF calls to your external security package are used to access permissions for user’s requests to menus, resources, and commands. This is enabled when $RMSXS-prefixed member is specified in the NPF Resource List Member field of a UAMS definition.
The following diagram shows the relationship between UAMS and SAF within an external security package. The $RMSXS-prefixed member can either be empty (as shown in the diagram) or contain NPF statements. Sample members are listed in the table in Sample NPF Members.
The following NPF members (with names prefixed by $RMSXS) indicate that an external security package is to be used:
Contains a special indicator—NPF will be bypassed in favor of an external security package.
Contains permissions for administrators—combined NPF and external security package.
Contains permissions for operators—combined NPF and external security package.
Contains permissions for network operators—combined NPF and external security package.
Contains permissions for monitors—combined NPF and external security package.
Sample security profiles are provided for each of the supported external security packages in the following libraries:
Specifies your site-specific data set name prefix.
Specifies your product version prefix.
Note: On z/VM systems, these profiles are on the vmid 293 G-disk.
Each library includes the following security profiles:
Specifies permissions for all groups of users for CA ACF2 versions earlier than Version 6.
Specifies permissions for all groups of users for CA ACF2 Version 6 and later.
Specifies permissions for all groups of users for CA Top Secret.
Specifies permissions for all groups of users for RACF.
To define the appropriate security profiles to an external security package, complete these steps:
The security requirements for the sample groups—$RMADMIN, $RMOPER, $RMNOPER, and $RMMON—are now defined to your external security package and will apply to users attached to these groups.
The supplied security members define each group’s access to functions and resources. These security members can be modified to suit your own security requirements. Use the syntax specified in the following sections to specify your own requirements for access to menu options, the knowledge base, system images, Automation Services commands, system commands, and product commands.
To control access to menu options, specify:
$RMMENU.menu-id.option-code
Identifies the menu. The ID of the main Primary Menu is $NM001. To display the ID of another menu, enter MENUID at the Select Option prompt.
Identifies the option (for example, A for the Administration and Definition option on the main Primary Menu).
Note: The asterisk (*) represents null, or one or more characters. Two asterisks (**) represent any suffix. This may not apply to your security system, in which case, you must use the equivalent wildcard character that does apply.
The knowledge base contains definitions of Automation Services components. To control access to knowledge base definitions, specify:
$RMDB.system-image-name.system-image-version.class-number. definition-name.action-type
Names the system image.
Identifies the version of the system image.
Identifies the class of component. The following table lists the valid classes. A product uses a subset of these classes.
|
class-number |
Component Definition |
|---|---|
|
01 |
System image |
|
02 |
Started task |
|
03 |
SNA group |
|
04 |
CICS transaction |
|
05 |
CICS file |
|
06 |
CICS database |
|
07 |
CICS link |
|
08 |
CONNECT:Direct manager |
|
09 |
CONNECT:Direct monitor |
|
10 |
Initiator |
|
11 |
Printer |
|
13 |
Spool |
|
14 |
JES line |
|
16 |
DASD |
|
17 |
USRCLS—user-defined resource class |
|
18 |
Tape or cartridge unit |
|
19 |
Batch job |
|
20 |
Job entry subsystem (JES) |
|
21 |
Internal resource |
|
22 |
FTS manager |
|
23 |
FTS monitor |
|
24 |
File transfer schedule |
|
25 |
FTP manager |
|
26 |
FTP monitor |
|
27 |
CONNECT:Mailbox manager |
|
28 |
CONNECT:Mailbox monitor |
|
29 |
Sysplex component |
|
30 |
Console message profile |
|
31 |
VM guest |
|
32 |
Linux image |
|
33 |
Linux application |
|
35 |
User profile |
|
36 |
Status monitor filter |
|
38 |
FTP policy rule set or rule |
|
39 |
IP Node Monitor group |
|
40 |
Command |
|
41 |
Logical state table |
|
42 |
IP node |
|
43 |
IP address space monitor |
|
44 |
Channel Interface Processor |
|
46 |
Open Systems Adapter |
|
47 |
Enterprise Extender |
|
48 |
Communications storage manager |
|
49 |
VIPA |
|
50 |
Availability map |
|
51 |
TCP/IP stack |
|
52 |
CICS monitor |
|
53 |
APPN/HPR |
|
54 |
Network control program (NCP) monitor |
|
55 |
SNA resource model template |
|
56 |
SNMP host details |
|
57 |
VTAM state |
|
60 |
Resource group |
|
61 |
Service |
|
62 |
CA-XCOM manager |
|
63 |
CA-XCOM monitor |
|
64 |
Monitoring attribute |
|
70 |
Macro |
|
71 |
Process |
|
74 |
Calendar criteria |
|
75 |
Calendar |
|
76 |
Calendar keyword |
|
78 |
Activity schedule |
|
80 |
Icon |
|
81 |
Icon panel |
|
90 |
Prompt list |
|
93 |
Rule set |
|
94 |
Message rule |
|
95 |
Message group rule |
|
96 |
Learnt message |
|
98 |
Timer rule |
|
9A |
Included rule set |
|
9B |
Initial action |
Note: Resource classes 30, 35, 36, 39, 40, 41, 56, 60, 61, 64, 70, 74 to 76, 78, 80, 81, 90, 93 to 96, 98, 9A, and 9B are independent of system images.
Identifies the component definition.
Identifies the action to be performed on the definition. Valid values are:
Creates a new definition.
Deletes an existing definition.
Updates a definition.
$RMDB.system-image-name.*.02.*.CREATE
You can control which functions a user can perform on a system image. To control access to system image resources, specify:
$RMSYS.system-image-name.system-image-version
Names the system image.
Identifies the version of the system image.
You can control whether a user can issue an Automation Services command on an Automation Services component. To control the use of these commands, specify:
$RMCMD.system-image-name.system-image-version. class-number.component-name.as-command-name
Names the system image.
Identifies the version of the system image.
Identifies the class of component. The table in Controlling Access to the Knowledge Base lists the valid class numbers.
If you want to restrict the use of a command on SNA resources in CA NetMaster Network Automation, specify 55 for the class number.
Identifies the component.
Names the command.
Note: For information about how to view the list of registered commands, see the Reference Guide.
The following list shows non-registered commands:
Synchronizes databases.
Enables a user to unload command replacement NCL procedures.
Transmits a system image or other database components.
The express setup facility calls $NMSEC with the command name SETUP to check if the user ID has authority to run the facility.
$RMCMD.system-image-name.*.24.*.*
To control the use of system commands, specify:
$RMSYCMD.system-command-name.operand-1.operand-2…operand-n
Names the system command.
Specifies the operands of the command.
To control the use of product commands, specify:
$RMNMCMD.product-command-name
Names the command. See the 3270 Online Help for the list of product commands.
When you issue a command from the OCS window or command entry panel, you issue the command under the control of your command authority level and the external security profile of the region. You do not normally issue the command under the control of your own security profile.
If you want to issue a command under the control of your own security profile, replace the command with an NCL procedure.
Note: This does not affect system commands that are already controlled by SAF.
To control the type of access to Customizer parameter groups, specify:
$RMICS.action.parameter-group-name
Specifies the type of access to the Customizer parameter groups. The access can be one or more of the following types:
Gets parameter group.
Files parameter group.
Actions parameter group.
Updates parameter group.
Browses parameter group.
Names the Customizer parameter group.
$RMICS.GET.*
| Copyright © 2012 CA. All rights reserved. |
|