Configuration Guides › Federation Security Services Guide › Federation Security Services Overview › Federation Security Services Process Flow › Flow Diagram for SSO Using SAML 1.x Artifact Authentication
Flow Diagram for SSO Using SAML 1.x Artifact Authentication
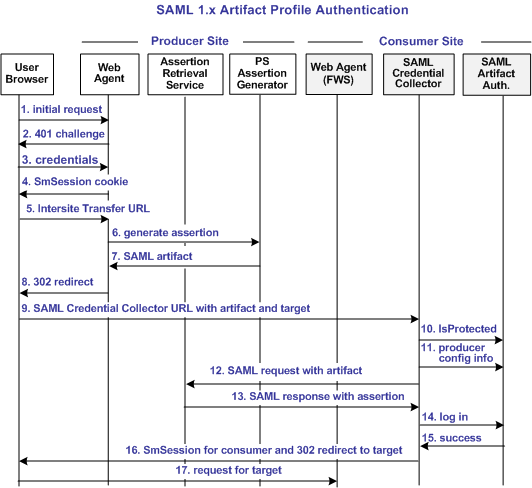
The following illustration shows the detailed flow between a user and the CA SiteMinder Federation Security Services components deployed at the producer and consumer sites. This set-up enables single sign-on between the sites. SAML artifact profile is the authentication method and the flow diagram assumes successful authentication and authorization at the producer and consumer sites.
Note: This flow applies to examples that do not use the SAML Affiliate Agent.
The process flow diagram for SAML 1.x Artifact Authentication follows.
Note: The SPS federation gateway can replace the Web Agent and Web Agent Option Pack to provide the SiteMinder Federation Web Services application functions. In the flow diagram, the Web Agent block would be the embedded Web Agent in the SPS federation gateway. For information about installing and configuring the SPS federation gateway, see the CA SiteMinder Secure Proxy Server Administration Guide.
The sequence of actions is as follows:
- The user makes an initial request to a protected page at the producer site.
- The Web Agent at the producer site responds with a 401 challenge to the user.
- The user submits credentials, such as user name and password to the Web Agent.
- The Web Agent issues a SiteMinder SMSESSION cookie to the browser of the user for the producer site domain.
- The user clicks a link to visit the consumer site. This link is referred to as the intersite transfer URL because it results in transferring the user to another site. The intersite transfer URL makes a request to the Web Agent at the producer site first. This URL contains the location of the SAML credential collector and the target URL to access at the consumer site.
- The Web Agent at the producer site handles the intersite transfer URL request by calling the assertion generator.
- The assertion generator generates a SAML assertion, places it in the SiteMinder session server and returns the SAML artifact for the assertion.
- The Web Agent responds with a 302 redirect to the SAML credential collector at the consumer with the SAML artifact and the target URL as query parameters.
- The browser makes a request to the URL for the SAML credential collector at the consumer site.
- The SAML credential collector handles the URL request by making an isProtected call to the SAML artifact authentication scheme.
- The SAML artifact authentication scheme returns the producer configuration information.
- The SAML credential collector uses the producer configuration information to make a SAML request to the assertion retrieval service at the producer. In this step, the SAML credential collector is acting as an HTTP client.
- The assertion retrieval service at the producer retrieves the SAML assertion from the session server and responds with a SAML response that contains the SAML assertion.
- The SAML credential collector makes a login call to the SAML artifact authentication scheme, passing the SAML assertion as credentials.
- The SAML artifact authentication scheme validates the SAML assertion. The authentication scheme looks up the user record based on the user mapping information configured for the scheme. The scheme returns a success reply. If the SAML assertion is not valid or a user record cannot be located, the scheme returns a failure reply.
- If the scheme returns a success reply, the SAML credential collector issues a SiteMinder SMSESSION cookie for the consumer domain to the browser. The SAML credential collector also issues a 302 redirect to the target URL. If the scheme returns a failure reply, the SAML credential collector issue a 302 redirect to a no access URL.
- The browser makes a request to the target URL, which is protected by the Web Agent at the consumer.
