

Touchpoint Security lets you secure touchpoints associated with business-critical hosts and hosts that contain sensitive data. You can secure such touchpoints against unauthorized access. You can create Touchpoint policies that specify selected users or a high-privileged group as the only identities that can execute an operator on that target. Policies specify identities that are authorized to execute certain operators on specified touchpoints. The operators that run programs and scripts are contained in specified operator categories.
In summary, CA EEM Touchpoint Security policies authorize specified identities to execute scripts in operators from specified categories on specified touchpoints in a specified environment.
Consider the following example snippet of a simple Touchpoint Security policy.
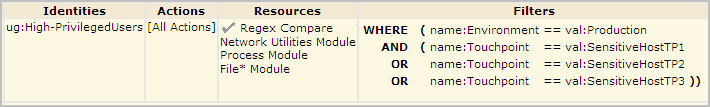
The example is a portion of a policy. The policy allows only users in the High-PrivilegedUsers group to execute any operator from specified categories on specified touchpoints in the Production environment. The example touchpoints are named SensitiveHostTP1, 2, and 3. Specified Access Control IDs include the Network Utilities module and the Process module (for Command Execution),. File* Module includes both File module for File Management and the File Transfer module.
Note: See Identify the Access Control IDs to Add as Resources.
A process with an operator target protected by a Touchpoint Security policy can finish successfully only it runs as an authorized user. The user under which the process runs is specified as an Identity in the policy. The policy identifies users by name or group membership, operators by the access control IDs associated with source categories, and touchpoints by name, environment, or both.
Touchpoint Security policies secure access to individual target hosts by controlling who executes operators on a specific touchpoint or host group. A process instance runs on behalf of a user. When the process executes an operator on a touchpoint or host group specified in a CA EEM Touchpoint Security policy, CA EEM attempts to authorize that user. CA EEM verifies that the user is specified as an Identity in a Touchpoint Security policy for that touchpoint. If the process instance is running on behalf of an unauthorized user, then the operator fails.
You specify sensitive hosts as touchpoints, proxy touchpoints, or host groups.
You can limit access to specified hosts to high-privileged users. You can grant access to a specified user or group that has been granted the following prerequisite access:
|
Copyright © 2014 CA.
All rights reserved.
|
|