

CA EEM defines permissions as Resource Class actions. You can, optionally, use filters to limit the actions that you allow a group or user. For example, you can scope permissions so that they apply to the assigned group in the configured environment only.
The following Filters example illustrates the use of ENVIRONMENT as the named attribute for the filter. Policies that are defined with the Access Policies type let you add filters.
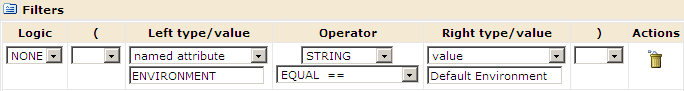
The actions in the following table belong to policies based on the referenced resource class.
|
Action Key |
Resource Class for Policy |
Named Attribute for Filter |
|---|---|---|
|
Object_List (List) Object_Read (Read) Object_Edit (Edit) Object_Delete (Delete) Object_Admin (Admin) |
Object |
SECURITY_CONTEXT_ID SECURITY_CONTEXT_GRP ENVIRONMENT OBJECT_TYPE |
|
Agenda_Control (Control) |
Agenda |
ENVIRONMENT |
|
Dataset_Inspect (Inspect) Dataset_Modify (Modify) |
Dataset |
ENVIRONMENT |
|
Process_Control (Control) Process_Monitor (Monitor) Process_Start (Start) |
Process |
SECURITY_CONTEXT_ID SECURITY_CONTEXT_GRP ENVIRONMENT |
|
Resources_Control (Control) |
Resources |
ENVIRONMENT |
|
StartRequestForm_Start (Start) StarRequestForm_Dequeue (Dequeue) |
Start Request Form |
ENVIRONMENT |
|
Execute |
TouchPoint Security |
ENVIRONMENT TOUCHPOINT |
|
Copyright © 2014 CA.
All rights reserved.
|
|