

Identity policies can define roles that are mutually exclusive and cannot be granted to the same user concurrently. For example, you can prevent a user manager who can grant raises from also being a salary approver.
To create an identity policy set that enforces segregation of duties, create an identity policy with the following settings:
|
Setting |
Value |
|---|---|
|
Apply Once |
Not enabled |
|
Compliance |
Enabled |
|
Policy Condition |
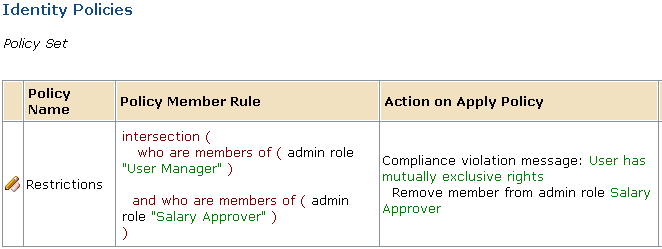
Use the "in <administrative-intersection-constraint>" option to define a set of conditions that violate a business policy. If a user meets all of the conditions, CA IdentityMinder takes the actions in the Action on Apply Policy field. For example, set the policy condition as follows: intersection (who are members of <some_role>) and who are members of <some_other_role> ) |
|
Action on Apply Policy |
The actions that CA IdentityMinder should take when the policy condition applies--for example:
|
The following figure illustrates the identity policy in this example.
|
Copyright © 2013 CA.
All rights reserved.
|
|