

CA Identity Governance implements RBAC standards without affecting an organization's on-going operation. CA Identity Governance implements the concept of a sandbox to separate CA Identity Governance's operation from the organization's on-going security environment (production server). The assumption is that when working with CA Identity Governance, existing access definitions must first be imported into a sandbox. A sandbox is an offline PC computer on which CA Identity Governance is installed where role discovery and audit activities are performed without affecting current operations of the organization. All work on discovering new or refining existing access definitions is performed in the CA Identity Governance environment.
CA Identity Governance defines roles as a group of users that have a common set of privileges. By users, CA Identity Governance refers to people or functions: employees, customers, suppliers, representatives, and so on. A resource is a specific right of access that may be an operation or object in formal RBAC terms. Thus, a resource can be as specific as a particular access right (Read/Write/Execute) to a specific file in a specific file system on a specific system, and it can also be used to provide a model for access to a computer system (such as, a user group on that system). A privilege is a connection between a user and a resource, indicating that this user possesses a specific access right. A role can include a set of users and a set of resources, with the semantics being that all users in the user set are allowed access to all resources in the resource set.
Most of CA Identity Governance's work is performed within a CA Identity Governance configuration that is automatically created when access data is imported into CA Identity Governance. By configuration, CA Identity Governance means a data structure that holds a snapshot of the definition of users, resources and roles (if already defined) and the relevant relationships (privileges) between them.
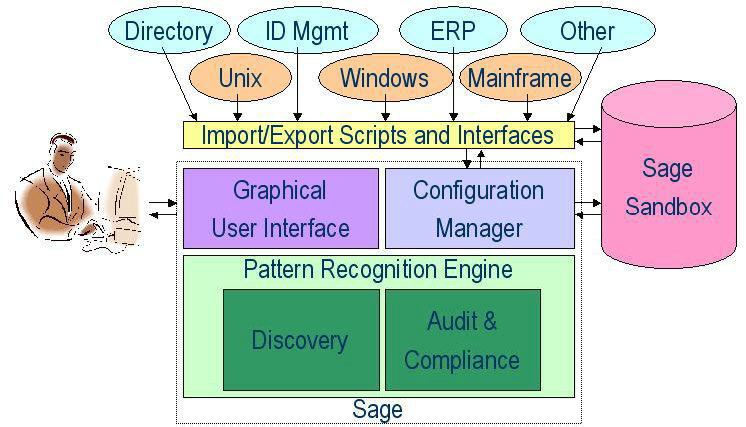
The following shows the CA Identity Governance architecture and how it relates to existing systems in your enterprise:
|
Copyright © 2014 CA.
All rights reserved.
|
|