

CA GovernanceMinder uses the following file types, as illustrated in the following diagram:
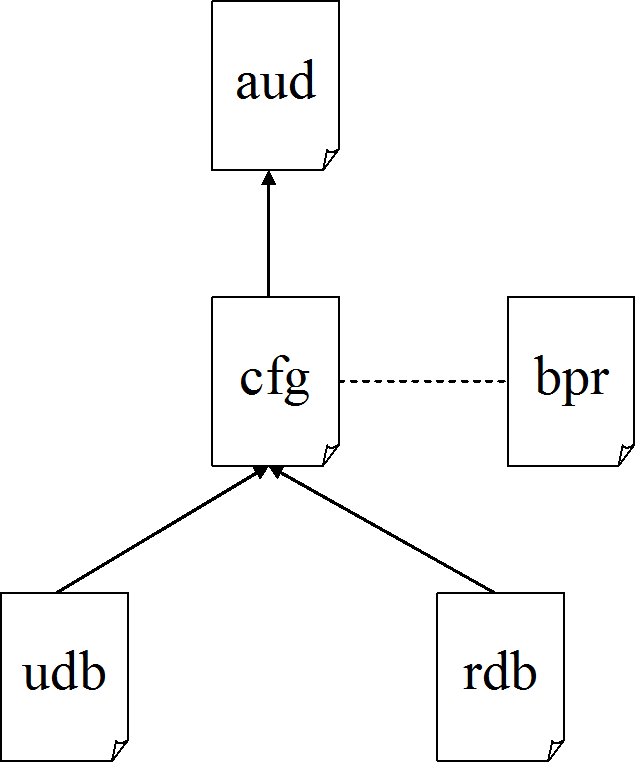
Contains one entry for each user that participates in any of our analyses. This entry usually contains such information as the user name, organizational unit (possibly in various levels), job description/code, status (internal/external, current/past employee), and so on), reporting structure, location (also possibly hierarchical, and so on). Typically, much of this information is brought from an HR system of some sort. Each user is identified by a unique ID called PersonID. The users database does not contain information about the user's privileges - this is the subject of our analyses and possible restructuring, and is therefore part of the configuration.
Complements the udb file, and contains one entry for each resource. A resource can be anything that a user may need access to, for example, a user group on a specific operating environment or application, access level to a certain file or share, permission to perform a transaction, and so on. The granularity in which resources are analyzed is up to the role engineer, and may vary. Furthermore, it is possible to perform different levels of analysis on the same set of systems.
The udb and rdb are relatively static and serve as the basis for possibly many configurations.
Represents a snapshot of privileges and role definitions. As such, the configuration includes information about roles – the third type of CA GovernanceMinder entity, and also about the four types of CA GovernanceMinder connections:
Represents a direct privilege of a user on a resource
Represents a user's membership in the role
Represents the permission of all of the role's users to the given resources
Represents a role hierarchy relationship, whereby users who are members of a parent role are automatically members of the sub-role, and therefore privileged to all of the sub-role's privileges.
Note: A configuration depends on its udb and rdb, but not all users/resources in the udb/rdb are necessarily included in a given configuration. Configurations that contain only a portion of the users/resources, for example, only the users of a certain organizational unit, are called partial configurations. There can be many configurations, representing various views, and using same udb and rdb.
Contains a set of alerts that were generated for a specific configuration at a specific time. The alerts can be generated using any of the CA GovernanceMinder auditing mechanisms. The AuditCard can then be updated and modified as part of the alert tracking process.
Contains a set of business process rules that can be used to audit one or more configurations. Each rule is typically a business constraint, such as "people that do X cannot do Y", or "only people that have a skill A can do B". Another common example of business process rules is segregation of duty principles, which restrict the ability of users to perform sensitive and critical tasks on their own without the involvement of other users. Policies are loosely tied to configurations, because same policy can be applied to multiple configurations and multiple policies can be applied to a single configuration. The result of applying one or more policies to a configuration is an AuditCard with the relevant violations as alerts.
|
Copyright © 2014 CA.
All rights reserved.
|
|