A Certificate Revocation List (CRL) is issued by a Certificate Authority to its subscribers. The list contains serial numbers of certificates that are invalid or have been revoked. When a request to access a server is received, the server allows or denies access based on the CRL.
Federation Manager can leverage CRLs for its certificate functions. For Federation Manager to use a CRL, the certificate data store must point to a current CRL. If Federation Manager tries using a revoked partner certificate, you see an error message. For legacy federation, the error message is in the SAML assertion. The message indicates that authentication failed.
Federation Manager supports the following CRL features:
Federation Manager stores CRLs in the certificate data store. File-based CRLs must be in Base64 or binary encoding. LDAP CRLs must be in binary encoding. Additionally, LDAP CRLs must include CRL data in one of the following attributes:
When a Certificate Authority publishes an LDAP CRL, it must return the CRL data in binary format, in accordance with RFC4522 and RFC4523. Otherwise, Federation Manager cannot use it.
Federation Manager does not validate an SSL server certificate against a CRL. The web server where Federation Manager is installed manages the SSL server certificate.
You are not required to have a CRL for each root CA in the system. If there is no CRL for the root CA, Federation Manager assumes that all certificates signed by that CA are trusted certificates.
The following figure shows the procedures for managing CRLs.
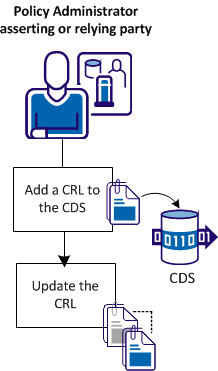
The CRL configuration steps are as follows:
| Copyright © 2012 CA. All rights reserved. |
|