

Native security uses the following three security tables to record security rules for access to inventory levels and functions:
Defines the environments to which you have access.
Defines the menu options available to you after access to an environment is obtained. Further, this table defines actions allowed within the environment, by user, for each system and subsystem.
Enforces naming conventions at the system/subsystem and element level.
The following figure shows how control points can control access to CA Endevor SCM processing functions by checking native security tables.
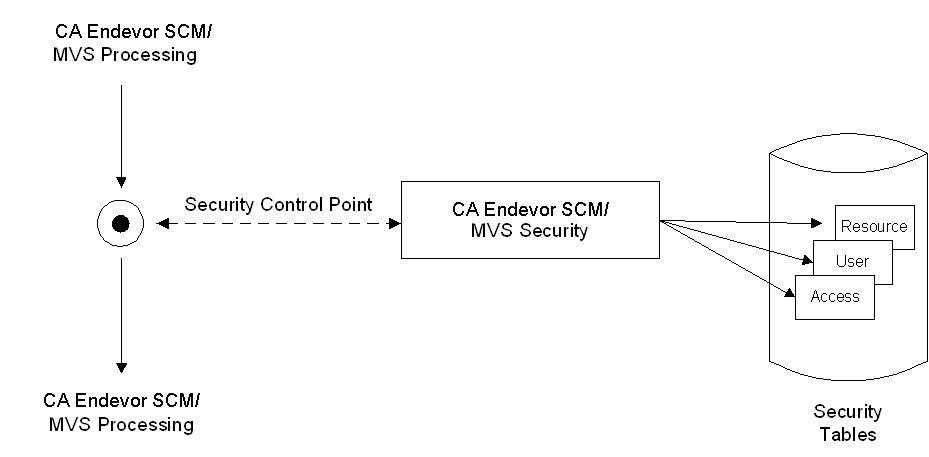
As previously illustrated, upon entry into the system, your access to CA Endevor SCM functions is controlled by CA Endevor SCM Security Tables or the CA Endevor SCM (ESI). Site security provides protection of system data sets.
|
Copyright © 2014 CA Technologies.
All rights reserved.
|
|