

The SAML Assertion Query step lets you obtain a SAML assertion from an identity provider for use in a Web Service Execution step that uses a WS-Security SAML 1.x Assertion Token.
Prerequisites: A cursory understanding of what type of SAML Assertion Query that you must perform. Obtain this information from either the developer of the system that uses SAML Assertions as the form of identity security or from the identity provider administrator.
Parameter Requirements: At a minimum, know:
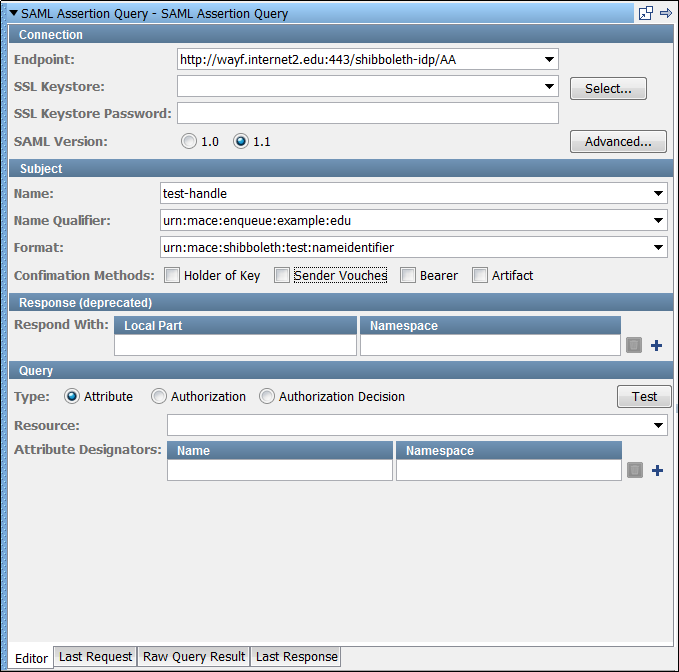
The SAML Assertion Query Editor has four tabs. The Editor tab lets you configure the query information. After you configure the query, you can test the query using the Test button in the Query section of the editor. After you test the query, you can view the raw request that was sent in the Last Request tab. You can view the raw SOAP response in the Raw Query Result tab. For example, if the query returned multiple assertions, you can see the assertions in the Raw Query Result tab. You can view the step response in the Last Response tab. The Last Response tab shows, for example, what is used in the Web Service WS-Security token.
The Advanced button lets you enter more information.
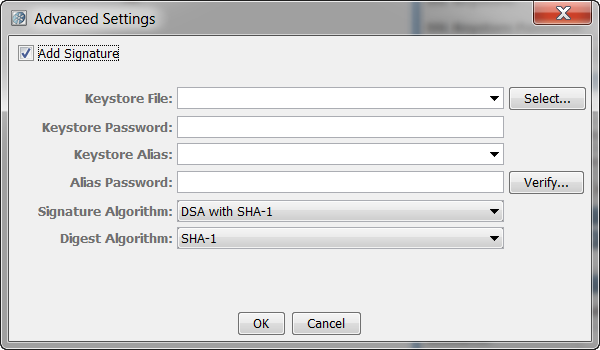
Select the Add Signature check box.
The location of the keystore file.
Enter the password for the keystore.
Enter an alias for a private key.
Leave empty or make the same as Keystore Password for PKCS #12 files.
Select DSA with SHA-1.
Values: SHA-1, SHA-256, SHA-384, SHA-512, RIPEMD-160, or MD5 (not recommended).
This information describes where the SAML Query API server is and how to connect to it.
The URL to the SAML Query API of the identity provider.
To use client-side identification certificates to connect to the endpoint, select the keystore file using the Select button. Or, select a previously entered item from the pull-down list or enter one manually.
The password for the SSL Keystore if used.
The SAML version to use to query the identity provider.
This information describes the recipient of a SAML assertion. The subject could be a user, user group, or other entity for which you want to provide an assertion about the current authorization/privileges.
The name of the entity (for example, username).
A group or categorization that is used to qualify the Name (for example, domain).
This field describes what format the name is being sent (for example, Full Name as opposed to Username).
Select which confirmation method types you want to include in the query. The query only returns assertions that contain at least one of the specified types. If you leave all types cleared, the query returns any assertion regardless of the confirmation method.
This information describes which assertion statements you want to be returned as part of the SAML Assertion. Response is deprecated as of SAML 1.1.
The element name (for example, AuthenticationStatement, AuthorizationDecisionStatement, and AttributeStatement).
The element namespace (for example, urn:oasis:names:tc:SAML:1.0:assertion).
Click Add ![]() to add more XML elements to the set to be returned.
to add more XML elements to the set to be returned.
Click Delete ![]() to remove any elements you have already added.
to remove any elements you have already added.
A description of which type of query to perform. The query types are:
An attribute query responds with a set of attribute statements. For example, it could tell you which groups a subject is a member of.
To limit your query to a specific resource (for example, a specific web service, domain, file) specify the resource name.
A name and namespace (like XML elements) identifies each attribute. You can filter the set of attribute statements that are returned by specifying each attribute type to be returned.
Example:
Name = urn:mace:dir:attribute-def:eduPersonScopedAffiliation, Namespace = urn:mace:shibboleth:1.0:attributeNamespace:uri)
Used to request authentication statements that are related to a specific Subject SAML Assertions.
This parameter limits your query to returning Authorization Statements that are for a specific authorization method.
Example:
urn:oasis:names:tc:SAML:1.0:am:X509-PKI, urn:oasis:names:tc:SAML:1.0:am:PGP, urn:oasis:names:tc:SAML:1.0:am:password
A set of predefined authorization methods is available from the pull-down list.
Used to request SAML Assertions for specific actions that a subject wants to perform, given the evidence.
To limit your query to a specific resource (for example, a specific web service, domain, or file), specify the resource name.
Specify at least one action for which to request authorization to perform (for example: login, view, edit) specified with a name (Data) and Namespace (like an XML element).
(Optionally) Specify one or more SAML Assertions to include with the Authorization Decision Query as advice to the Identity Provider. Specify the property that holds the SAML Assertion XML. To use the response from a previous step (for example, another SAML Assertion Query or Parse Text step) use lisa.<stepname>.rsp.
Optionally specify assertion reference IDs.
|
Copyright © 2014 CA Technologies.
All rights reserved.
|
|