

CA DataMinder is able to quarantine emails until they have been approved by an appropriate representative.
If you want to quarantine emails encrypted by Voltage SecureMail, you must deploy the CA DataMinder Quarantine Manager and a Voltage SecureMail gateway.
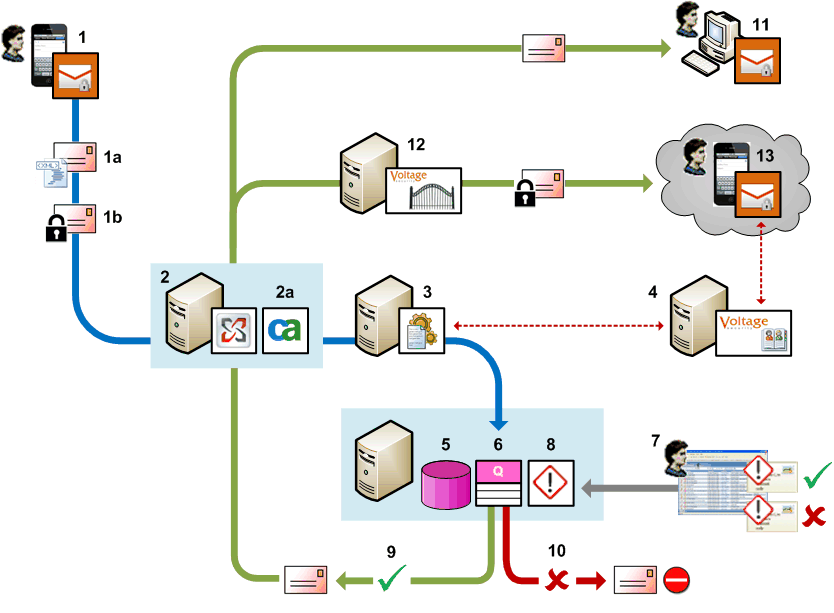
In the example below, a user sends a secure email to an internal recipient and an external recipient. CA DataMinder detects the email, applies policy, and quarantines the email. When the email is released from quarantine, the version addressed to an external recipient is re-encrypted by the Voltage SecureMail gateway before that version is delivered. The version addressed to an internal recipient is delivered directly and is not re-encrypted.
Note: For simplicity, this diagram omits a policy engine hub and shows the Exchange server agent passing emails to a single CA DataMinder policy engine.
Example: SecureMail integration and quarantined emails on an Exchange server
An employee (1) sends a secure email from their mobile device. If they use a Voltage SecureMail clientless solution, the email is not encrypted yet, but contains an x-header to indicate that encryption is required (1a). If they use a Voltage SecureMail end-to-end solution, the email is encrypted before it leaves the mobile device.
When the secure email passes through the Exchange server (2), the Exchange server agent (2a) intercepts the email and passes it to a policy engine (3) for analysis.
The policy engine establishes a secure connection to the Voltage SecureMail server (4), which sends back an unencrypted version of the email. The policy engine analyzes the email and applies a Quarantine action. A decrypted version of the email is saved in the CMS database (5). The email is also saved in a quarantine queue (6).
iConsole reviewers can search for quarantined emails and release or reject them (7).
The Quarantine Manager (8) regularly checks the quarantine queue and forwards released emails to their intended recipients (9). At this stage, emails released from quarantine are unencrypted but include an 'encryption request' x-header. Rejected emails are not forwarded (10).
When released emails pass through the Exchange server, any emails addressed to internal recipients are sent directly, unencrypted, to the recipient (11).
Emails addressed to external recipients are routed through a Voltage SecureMail Gateway (12). The Gateway detects the 'encryption request' x-header and re-encrypts the email before sending it to the intended recipient (13). To decrypt the email, the recipient must authenticate themself to the Voltage SecureMail server (4).
|
Copyright © 2014 CA.
All rights reserved.
|
|