

Platform Deployment Guide › Advanced Encryption Mode › Advanced Encryption Certificates › Deployment Architecture
Deployment Architecture
The following diagram summarizes the FIPS 140-2 implementation.
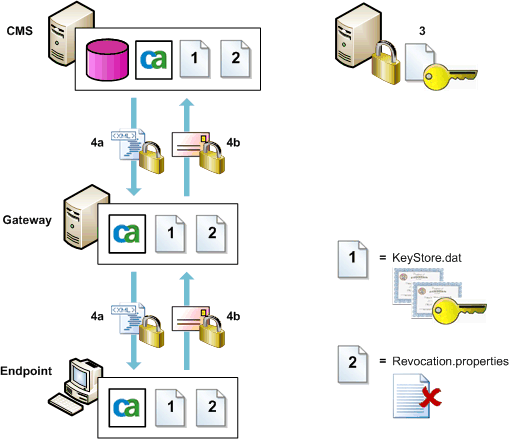
Deployment Architecture: Advanced Encryption Mode
- KeyStore.dat. This is the Key Store file. It contains the root certificate, the enterprise certificate, and the private key for the enterprise certificate key pair. A copy is held on each machine in your CA DataMinder enterprise.
- Revocation.properties. This is the Revocation List file. It contains a list of all revoked enterprise certificates. A copy is held on each machine in your CA DataMinder enterprise.
- Root certificate private key. This private key must be kept separate from your CA DataMinder enterprise on a secure server. It is used when you create replacement enterprise certificates.
- Encrypted sensitive data. This includes infrastructure changes such as policy edits or user account updates (4a) replicated from the CMS to gateway servers and endpoint machines. It also includes captured data, such as emails, files or Web activity (4b) replicated from endpoint machines and gateway servers to the CMS.
Copyright © 2014 CA.
All rights reserved.
 
|
|


