

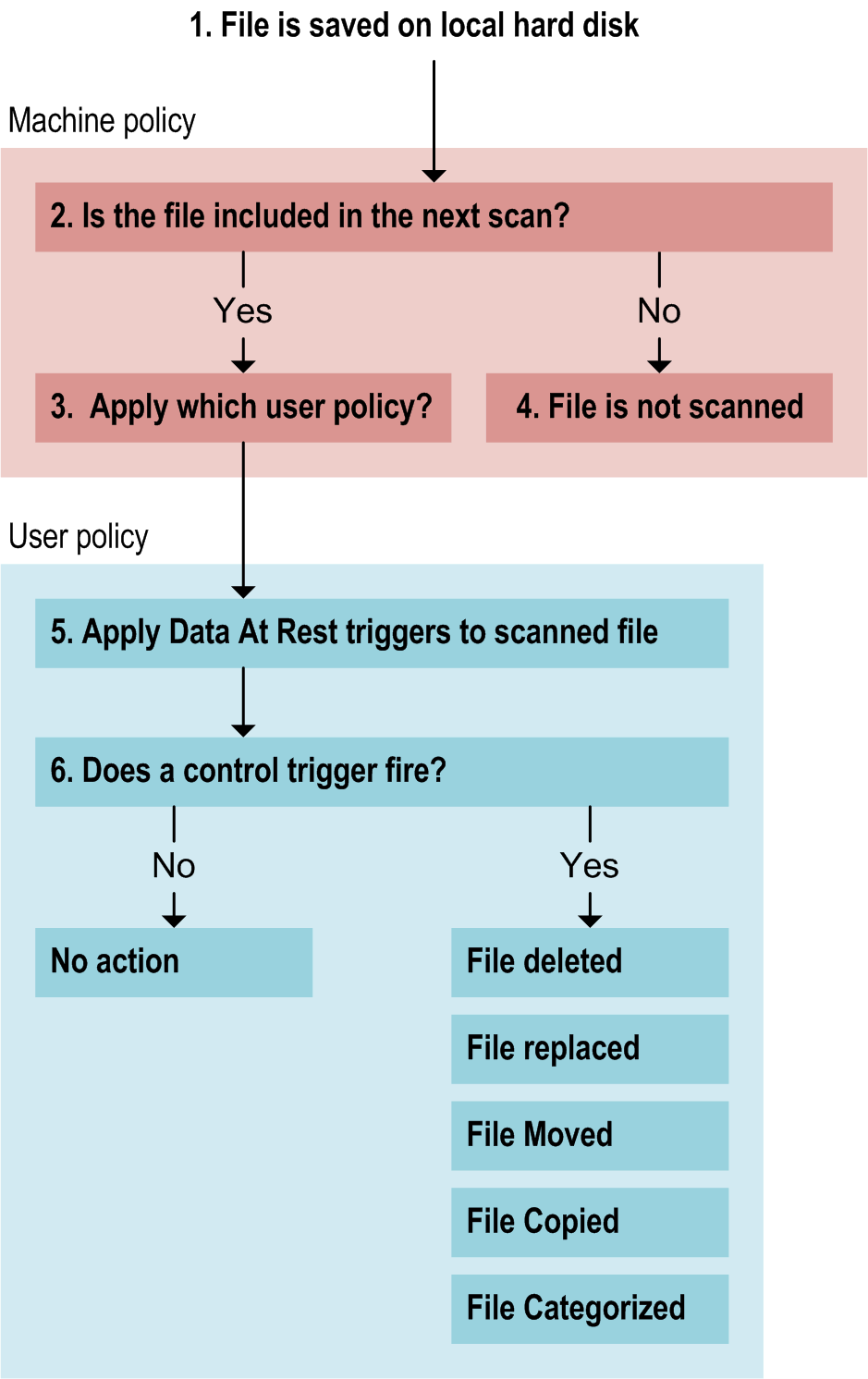
In the diagram below, a user saves a file to the local hard disk (1). When the next scheduled file scan runs, the CFSA checks machine policy to determine which files and folders to include (2) and which user policy to apply (3). Files implicitly or explicitly excluded are not scanned (4).
When the scan runs, CFSA applies Data At Rest triggers to the scanned files (5). If a control trigger fires, the CFSA applies an action to the scanned file (6). For example, they can categorize files based on their text content, and delete, replace or move unauthorized files.
|
Copyright © 2014 CA.
All rights reserved.
|
|