

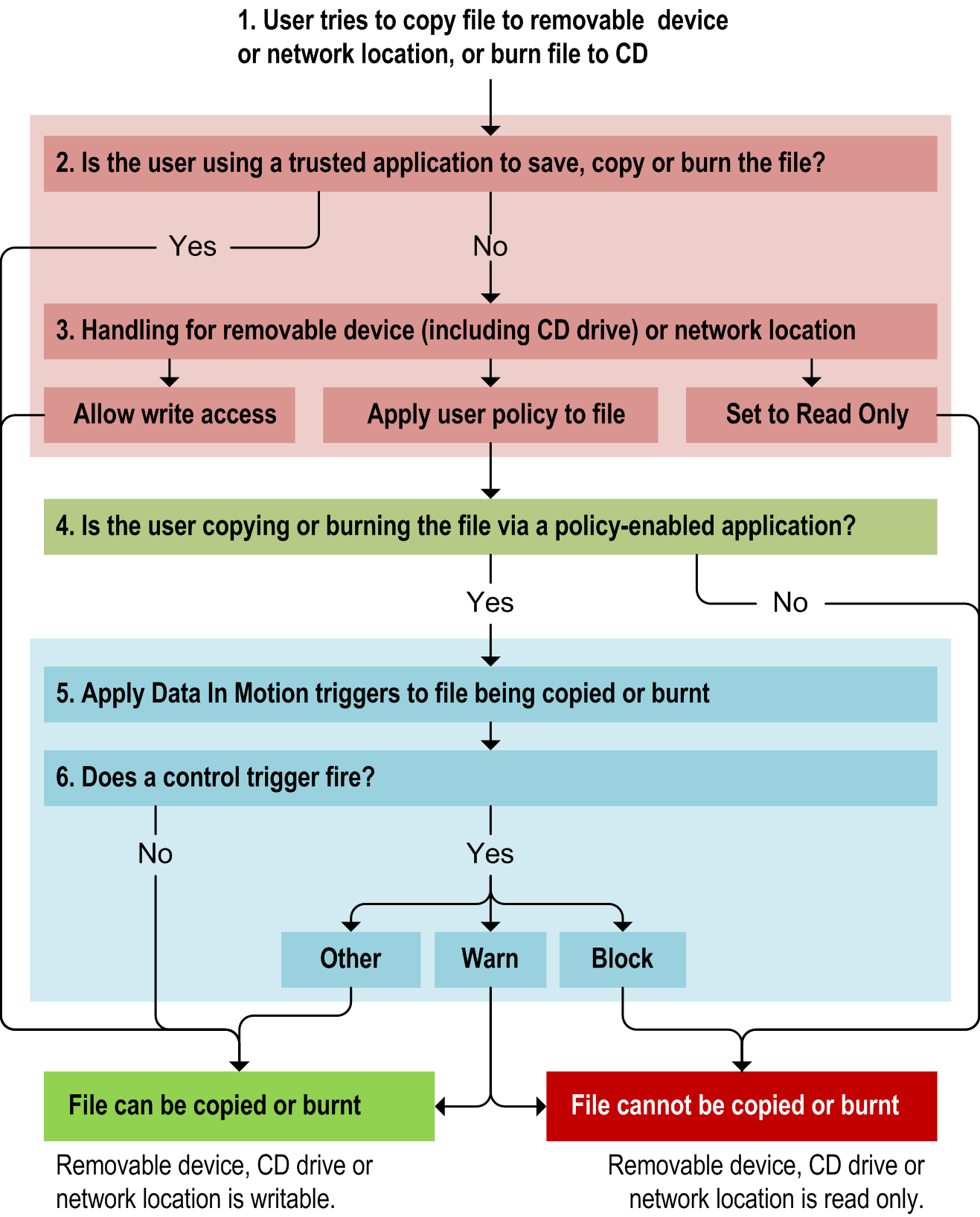
In the diagram below, a user tries to copy a file to a removable device or network location, or burn it to a CD (1). First, the CFSA checks whether the user is using a trusted application (2). If they are, it permits the file to be copied or burnt.
If the user is not using a trusted application, the CFSA checks the device, CD drive or location handling (3). If set to ‘allow write access’, file copying or burning is allowed; if it set to ‘read only’, the file is blocked.
Alternatively, if the handling is set to ‘apply user policy’, the CFSA checks whether a policy-enabled application is being used to copy or burn the file (4):
|
Copyright © 2014 CA.
All rights reserved.
|
|