

Policy Guide › What Is in a User Policy? › Actions
Actions
A user policy contains almost a hundred actions, covering all the main channels (email, Web, files, and so on). For each channel, there are also separate sets of control actions and capture actions.
- A control action defines how CA Data Protection intervenes when a control trigger fires. In particular, the Intervention setting defines the action you want CA Data Protection to take. For example, if an unauthorized attachment causes an email control trigger to fire, you can configure the Intervention setting to block the email or warn the user. Likewise, if a file scan causes a Data At Rest control trigger to fire, you can, for example, delete the unauthorized file or move it to an approved location.
- A capture action determines how much data is captured when a capture trigger fires. For example, you can choose whether to capture Web page images or email attachments.
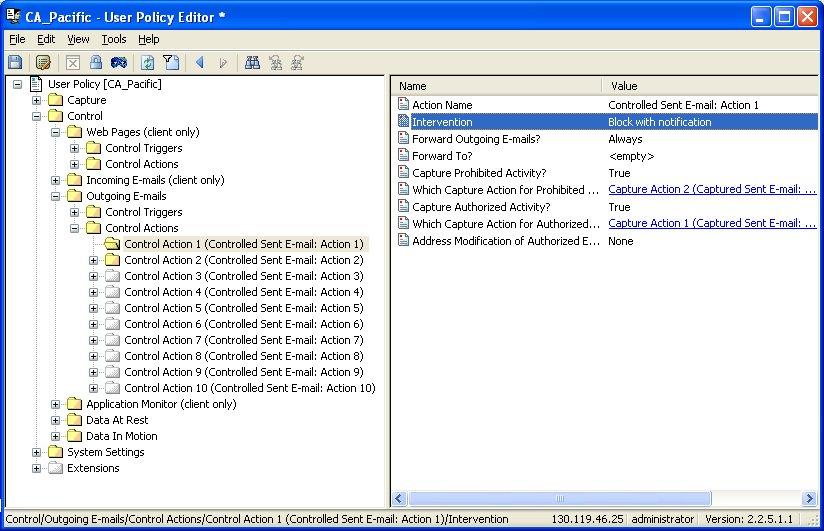
User Policy Editor, example control actions
More information:
Email Actions
Data In Motion Actions
Data At Rest Actions
Application Monitor Actions
Control Action Precedence
Copyright © 2015 CA Technologies.
All rights reserved.
 
|
|


