

Every day, CA Data Protection server and endpoint agents analyze thousands of events. Most of these are benign and do not need to be under policy control. So how does CA Data Protection separate those events that require policy from those that do not without causing massive disruption to an organization's daily work?
When CA Data Protection detects an event, whether it is an email, IM conversation, a print job, or a file, it goes through the following steps:
Typically, each employee has their own user account. If CA Data Protection identifies an employee as the event owner, it can quickly locate that employee's user account.
For events that cannot be associated with an employee, such as emails sent from outside your organization or files stored on your network, CA Data Protection typically assigns a default owner. This default owner corresponds to a 'system' user account (such as the External Sender or DefaultFileUser) rather than the policy for an actual user.
This process of associating the owner (1) with a CA Data Protection user account is very fast. Each CA Data Protection policy engine contains a record of the entire user hierarchy (2), and this record is continually kept up to date. Each endpoint agent identifies the relevant user account when the user first logs on. CA Data Protection applies that account's user policy to the event.
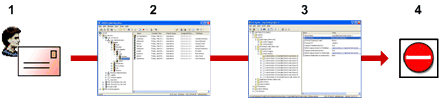
Policy processing procedure: CA Data Protection associates the event owner (1) with an account in the CA Data Protection user hierarchy (2). It then applies this account's policy (3). If a policy trigger fires, it immediately applies the appropriate action, such as a blocking (4).
It applies the control actions in order of priority. The order in which multiple control actions are applied is determined by the control action number. The control action with the lowest number takes precedence. For example, Action 1 always gets applied before Action 2 or Action 3.
|
Copyright © 2015 CA Technologies.
All rights reserved.
|
|