

The agent section of the UNAB configuration file (in the uxauth.ini file) defines the debugging information collected by the agent at run time. By default, UNAB collects debug information in the following file, where UNABInstallDir is the directory in which you installed UNAB:
UNABInstallDir/log/debug/agent_debug
The UNAB agent logs debug messages in the debug file when the uxauthd daemon starts, so long as the debug mechanism is enabled in the UNAB configuration file.
When you use the -debug option to start UNAB, a debug message appears in the user console.
As a UNAB administrator, you manage enterprise user access to the UNIX endpoints. You integrate UNAB with Samba to let the Active Directory domain users access the shared resources on the UNIX endpoints.
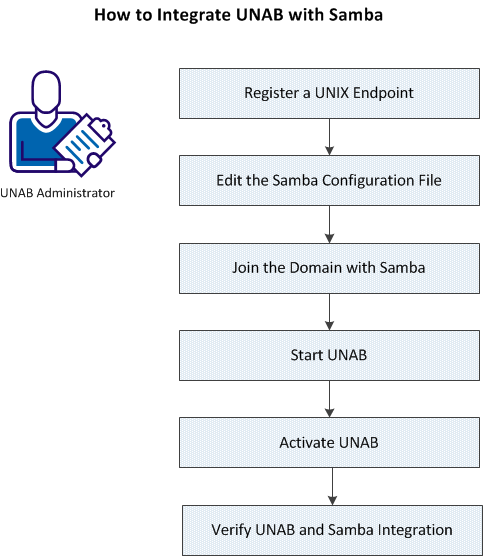
The following workflow provides an overview of the process:
Note: You can configure UNAB and Samba to work on the same endpoint in any sequence.
Verify the following prerequisites before you integrate UNAB with Samba:
Note: Install UNAB and Samba on the same UNIX endpoint.
You register a UNIX endpoint in the Active Directory to let Active Directory users log in to the UNIX endpoint.
Perform the following action:
# <InstDir>/uxauth/bin/uxconsole -register [-d domain] [-v level] [-n] -sso
Registers a UNIX endpoint in the Active Directory.
Defines the domain name of the Active Directory.
Defines the verbose level that you prefer during the installation process.
Specifies that the uxauthd agent will not run after the registration process completes.
Specifies that the uxconsole manages Kerberos files for Single Sign On (SSO).
You have registered a UNIX endpoint in the Active Directory in the SSO mode.
Example: Register a UNIX Endpoint in the Windows 2008 Active Directory Domain
The following uxconsole utility registers a UNIX endpoint (say UX-endpoint) with the Windows 2008 Active Directory in SSO mode. The Windows 2008 Active Directory domain name is corp.example.co.il. The Kerberos Single Sign On (SSO) service authenticates the user once. The user can log in to multiple UNIX endpoints using the same user credentials. The verbosity level is set to 3. The command -n indicates that the UNAB agent will not run after the registration process completes.
# /<InstDir>/uxauth/bin/uxconsole -register -sso -n -v 3 -d corp.example.co.il
You add Kerberos as the authentication method in the Samba configuration file. Samba authenticates the Active Directory users using Kerberos.
Follow these steps:
# vi/etc/opt/Samba/smb.conf
kerberos method = system keytab
You have edited the Samba configuration file.
You join a UNIX endpoint to the Active Directory domain using Samba.
Follow these steps:
# /opt/samba/bin/net ads join -U Administrator
Joins a UNIX endpoint to the Active Directory domain.
Specifies the domain administrator with privileges for adding a UNIX host to the domain.
# /sbin/init.d/samba start
# ls -l <path of the shared files on the UNIX endpoint>
You have joined a UNIX endpoint to the Active directory domain using Samba.
You start UNAB to enable the Active Directory users log in to the endpoint.
Follow these steps:
./uxauthd.sh start
The UNAB daemon starts.
You activate UNAB on a UNIX endpoint to let UNAB authenticate the Active Directory users.
Follow these steps:
<InstDir>/uxauth/bin
./uxconsole -activate
Specifies that login is activated for the Active Directory users.
You have activated UNAB on a UNIX endpoint.
You now verify the UNAB and Samba integration.
Follow these steps:
# /<InstDir>/uxauth/bin/uxconsole -status -detail
The following example shows a sample output. Here we consider that the Active Directory users in the corp.example.co.il domain access the shared files on the UX-endpoint endpoint.
CA Access Control UNAB uxconsole v12.55.0.945 - console utility
Copyright (c) 2010 CA. All rights reserved.
Client's site - Default-First-Site-Name
Registration domain - corp.example.co.il
DCs - corpdc1, corpdc2
User search base - DC=corp,DC=example,DC=co,DC=il
Group search base - DC=corp,DC=example,DC=co,DC=il
UNAB mode - full integration
UNAB status - activated
Agent status - running, pid = 22967
FIPS only mode - no
Kerberos configuration - standard
Time sync - disabled
Nested groups ACL - enable login by nested groups
Enterprise policy - login@UX-endpoint.corp.example.co.il#05 (updated: Sun May 6 10:08:17 2012)
Local policy - disabled
Default login access - deny
AD Unix users - 236 (updated: Sun May 6 09:55:41 2012)
AD Unix groups - 101 (updated: Sun May 6 09:55:41 2012)
AD Windows groups - 6339 (updated: Sun May 6 09:55:41 2012)
Migration - not migrated
CA Access Control - installed
Include AD users and groups in AC ladb : yes
Display AD names in AC Audit : no
Support AD non-Unix groups in AC: yes
PAM authentication in AC utilities : yes
AC Watchdog monitors UNAB agent : yes
# id tstuser
You have configured UNAB to work with Samba. The Active Directory users can log in to the UNIX endpoints using Samba and can access the shared resources. Samba authenticates users with the Kerberos authentication service.
|
Copyright © 2013 CA Technologies.
All rights reserved.
|
|