

To configure CA ControlMinder for your auditing requirements, you must first understand how auditing works. Auditing lets you keep track of access requests (events) that CA ControlMinder intercepted. You can use this data to meet with compliance requirements, to analyze and refine your access rules for your security requirements, or to monitor access requests.
The process CA ControlMinder follows to record audit events in the log depends on the type of event it intercepts:
Note: Intercepted login events (TERMINAL class), and audit records generated by user traces, are not cached; they always follow the auditing process for interception events.
Note: CA ControlMinder intercepts an event only if the appropriate class is active, and the database contains a rule anticipating this event.
An interception event is an event that CA ControlMinder encounters for the first time and for which no authorization information or audit information exists in the kernel cache.
To log audit records, CA ControlMinder performs the following actions and causes these effects for an interception event:
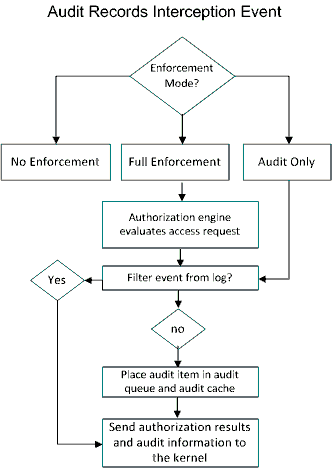
CA ControlMinder writes an audit item only if the audit property for the resource or accessor is set to audit the resulting event and the audit filter file is not set to filter this event.
CA ControlMinder writes an audit item only if the audit filter file is not set to filter this event. The authorization result in this mode is always P (permitted).
Note: Intercepted login events (TERMINAL class), and audit records generated by user traces, are not cached; the authorization engine always writes audit records for these events.
|
Copyright © 2013 CA Technologies.
All rights reserved.
|
|