

As a security administrator, modifying access rights for resources within your scope is a task that you regularly perform. This task is important because it:
This example describes how you can use CA Chorus and CA Top Secret to identify and correct an access rights problem, and then verify that you have corrected the problem.
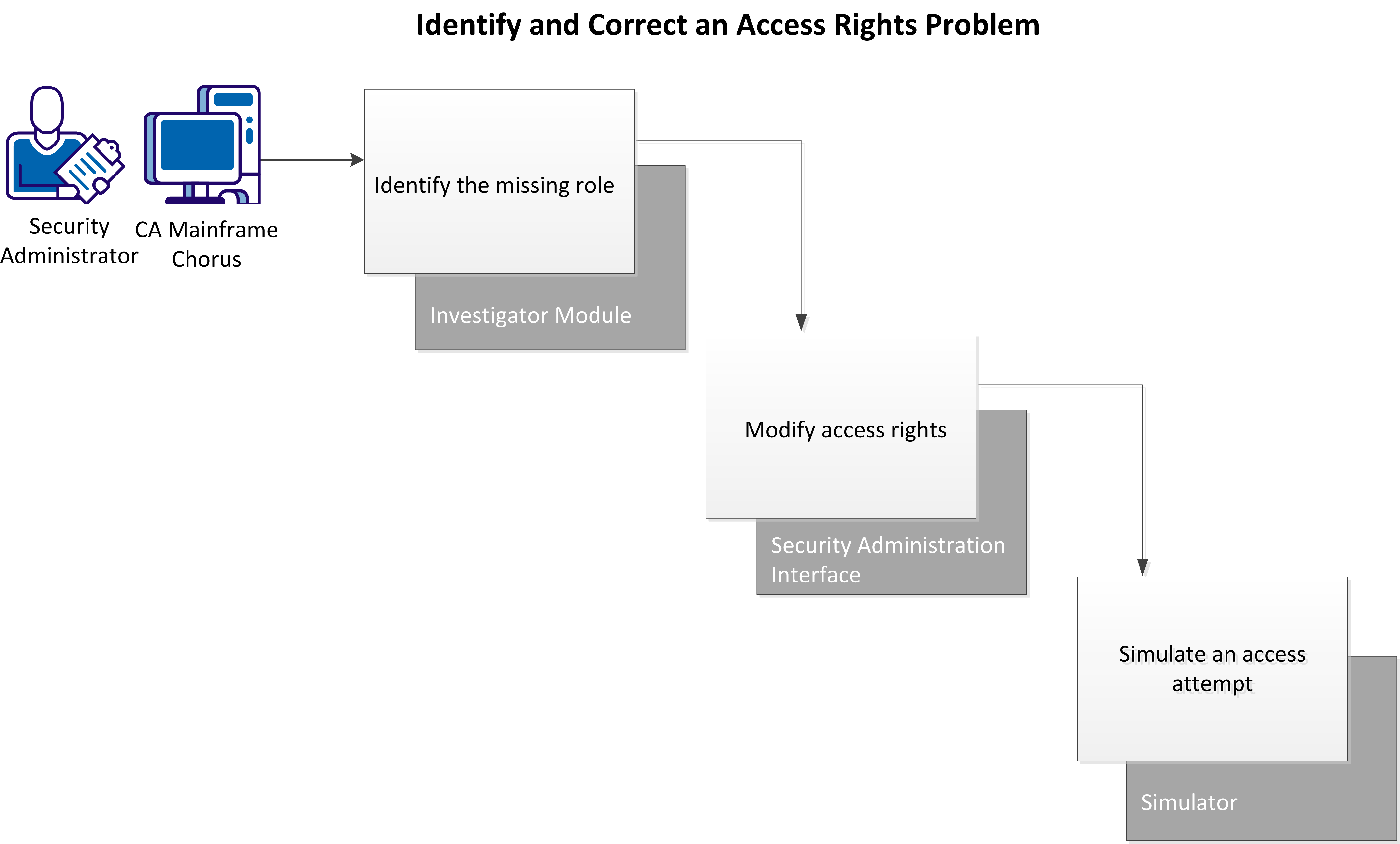
In this example, you have just received a service desk ticket with the following information:
Your research indicates that the employee needs read access to a particular data set.
Perform these tasks to identify and correct the access problem:
|
Copyright © 2013 CA Technologies.
All rights reserved.
|
|