

Latest version: 1.0.20-1
The WS_API application provides a web service interface to one or multiple grids through a Representational State Transfer (REST) based service. Any one of the following access methods can be used with the WS_API REST interface:
|
Property Name |
Type |
Description |
|---|---|---|
|
usr_ip |
IP |
This is the IP address at which the WS_API application provides services to users through HTTP or HTTPS based requests. This property is mandatory. |
|
net_ip |
IP |
This is the IP address that is used by the WS_API application to access any public network address. This property is mandatory. |
|
netmask |
IP |
Network mask for the network on which vpn_ip, usr_ip and net_ip reside. This property is mandatory. |
|
gateway |
IP |
Address of IP gateway to be used to route traffic. This property must be specified to access the WS_API application from hosts outside of the IP network on which WS_API is running. Use 0.0.0.0 to disable. This property is mandatory. |
|
dns1 |
IP |
IP address of a DNS server for host name resolutions. This property is mandatory. |
|
dns2 |
IP |
IP address of a backup DNS server for host name resolutions. Default: 0.0.0.0 |
|
allowed_hosts |
String |
Allowed IP address or range of IP address's in CIDR format. Default: 0.0.0.0/0; (allow all) |
|
http_mode |
String |
This specifies what kind of HTTP requests are served by the API on the usr_ip. Valid values: https, http, both. If set to http, simple HTTP based requests are served by the API. When set to https only Secure HTTP requests based on SSL v3.0 encryption are served by the REST API. If set to both all HTTP and HTTPS requests are served. Default: https. This property is effective only for requests that are served using the in appliance (that is has no effect when VPN is used). If the mode is set to http, be aware that all the traffic is plain text. It is highly recommended to set allowed_hosts property for the IPs that will be issuing API requests. |
|
opts |
String |
Arguments for SSL configuration may be provided to the application through the opts property as a comma-separated name=value pairs. It is not required to set this property in simple HTTP mode that is, when http_mode=http. If any of the arguments are not specified, then an empty value is assumed. Default: Empty (not used) ssl_country - The name of the country to be used in the generated SSL certificate. ssl_state_province - The name of the state or province to be used in the generated SSL certificate. ssl_locality - The name of the locality to be used in the generated SSL certificate. ssl_org_name - The name of the organization to be used in the generated SSL certificate. ssl_org_unit - The name of the organization unit to be used in the generated SSL certificate. ssl_common_name - The name or the URL to be used in the Common Name field in the generated SSL certificate. ssl_email_address - The email address to be used in the generated SSL certificate. ssl_export_pass - The password to be used for pkcs12 formatted client certificate to be imported into client Web Browser. |
|
vpn_ip |
IP |
This is the IP address at which the WS_API application provides services to the users through a secure VPN tunnel. Default: Empty |
|
vpn_ports |
String |
List of ports to access the web services API. These ports will be allowed through the VPN tunnel and firewall rules. Ports 80 and 443 are typically all that is needed. Default: 80,443 |
|
vpn_type |
String |
Type of the VPN tunnel to establish. Possible values are: certificate - A VPN tunnel is established using SSL client and server certificates for authentication and encryption with OpenVPN. The server certificate is generated automatically if not present. The client certificate must be generated manually with the /appliance/security.sh script located on the in_vpn appliance in the /server/ subdirectory of the conf volume. Copy the generated certificate into the remote VPN client appliance inside the /client/ subdirectory on the data volume or nfs-mounted volume. shared secret - A VPN tunnel is established using a shared secrets file with OpenVPN. This file is automatically generated on the in_vpn appliance if not already present. The file is in the /server/ subdirectory of the conf volume as secret.key. This file must be copied on the remote client VPN appliance into the /client/ subdirectory on the data volume or nfs-mounted volume. ssh key - An SSH tunnel is established using OpenSSH key files for authentication. Key files are generated on the in_vpn appliance in the /server/ subdirectory of the conf volume. The client key file must be copied into the /client/ subdirectory of the data volume or nfs-mounted storage in the remote VPN client appliance. ipsec certificate - IPSec tunnel using certificates is established between instances of the in_vpn and remote VPN client appliance. The server certificate is generated automatically if not present or may be generated with the /appliance/security.sh script in the /server/ subdirectory of the conf volume. The client certificate must be generated manually with the /appliance/security.sh script located on the in_vpn appliance. Copy the generated certificate into the /client/ subdirectory on the data volume or nfs-mounted volume of the remote VPN client appliance. Default: certificate |
|
vpn_authpath |
String |
Authentication information for the tunnel. For the shared secret mode of operation, this is a relative path to the shared secrets file on the data volume (ex. "secret.key" for a "client/secret.key" file). If the tunnel is ssh key, this property specifies the path to the ssh public (for VPN server) or private (for VPN client) key file (for example, "/1/ssh.key" for a /client/1/ssh.key public key file). The path includes the file name. Default: Empty |
|
vpn_standby |
Int |
Specifies whether VPN access is enabled on application start. If non-zero, VPN access is disabled, otherwise it is enabled. The VPN access can be enabled/disabled at runtime by manually starting/stopping the VPN appliance. Default: 1 (VPN access is disabled). |
|
in_standby |
Int |
Specifies whether access to the REST API is permitted through regular HTTP or HTTPS based connections. When this property is set to 1 and vpn_standby is set to 0 only VPN tunnel based access is permitted. Access through in can be enabled/disabled at runtime by manually starting/stopping the in appliance. Default 0 (regular HTTP and HTTPS access is enabled). |
Important! The IP addresses configured in the vpn_ip, usr_ip and net_ip properties must be IP addresses available on your CA AppLogic® for System z grid. You can find them, together with the netmask, gateway, and DNS servers on the dashboard of your grid. We are working to make it possible for CA AppLogic® for System z to provide these addresses automatically.
"WS_API" Application
|
Resources |
Min |
Max |
Default |
|
CPU |
0.55 |
76 |
1.1 |
|
Memory |
992 MB |
134 GB |
1.656 GB |
|
Bandwidth |
7 Mbps |
12.5 Gbps |
730 Mbps |
The application itself uses several volumes. They are part of the application and are already configured into the appliance instances.
|
Volume |
Size |
Description |
|
code |
50M |
This volume is used to store the API application's code and scripts. This volume is assigned to the WEB64 appliance. By default, a populated volume called 'code' is supplied for this application to use. |
|
conf |
50M |
This volume is used to store all the configuration data for the Web Service API application. This includes the "vdcs.conf" that is populated by the user to contain the following information:
This volume is assigned to a NAS appliance. By default, a populated volume called 'conf' is supplied for this application to use. |
|
log_data |
50M |
This volume is used to store logging data for the API server. It is also used to store temporary files required by the API application. This volume is assigned to the NAS appliance. By default, a populated volume called 'log_data' is supplied for this application to use. |
Before starting the WS_API application, it needs to be configured to access the grids that are going to be managed through the web service interface. This involves creating a vdcs.conf file inside the data sub-directory on the conf volume. A pair of private/public keys need to be created and a user needs to be setup on the targeted grid controller with the generated public key. For information about how to populate vdcs.conf and how to setup ssh keys and create a grid user for the web service API see the configure section.
The WS_API can be configured to work in one or a combination of the following modes:
Using HTTP
In this mode, the REST API can be accessed through the regular HTTP based interface.
For example, curl "http://usr_ip/api/v1/app/list?vdc=controller_name".
To start the application to work in this mode, it is required to set the mandatory properties to appropriate values and the http_mode property to http. For more information about how to set the application up to work in this mode,refer to the configure section.
Using HTTPS
In this mode, the REST API can be accessed through the Secure HTTP based interface.
For example, curl -k -E /path/to/client_key.pem "https://usr_ip/api/v1/app/list?vdc=controller_name".
To start the application to work in this mode, it is required to set the mandatory properties to appropriate values and the http_mode property to https. You may also set the opts property with the options shown in the properties table above for your certificate to be signed accordingly. After the application is started successfully, the client certificates must be copied from the ssl-keys subdirectory within the conf volume to the client application or browser to be used to access the WS_API. For more information about how to set the application up to work in this mode, refer to the configure section.
Using vpn tunnel
In this mode, a secure VPN tunnel is created between the in_vpn VPN server within the application and a VPN client on the client side. Once the tunnel is successfully created using one of the different VPN tunneling types available, the REST API can be accessed through the regular HTTP based interface.
For example, curl "http://usr_ip/api/v1/app/list?vdc=controller_name".
To start the application to work in this mode, it is required to set the mandatory properties to appropriate values, set the vpn_ip property and set the vpn_standby to 0. By default, vpn_ports is set to 80,443 to allow connections to ports 80 and 443 (http and https respectively) and vpn_type is set to certificate to allow a VPN client to connect to the VPN server in the application using a SSL certificate based tunnel. You may also set the in_standby property to 1 so that only requests through the VPN tunnel are allowed. Any API requests from outside of the VPN tunnel are dropped. For more information about how to set the application up to work in this mode, refer to the configure section.
The Web Services 'WS_API' application infrastructure has the following components:
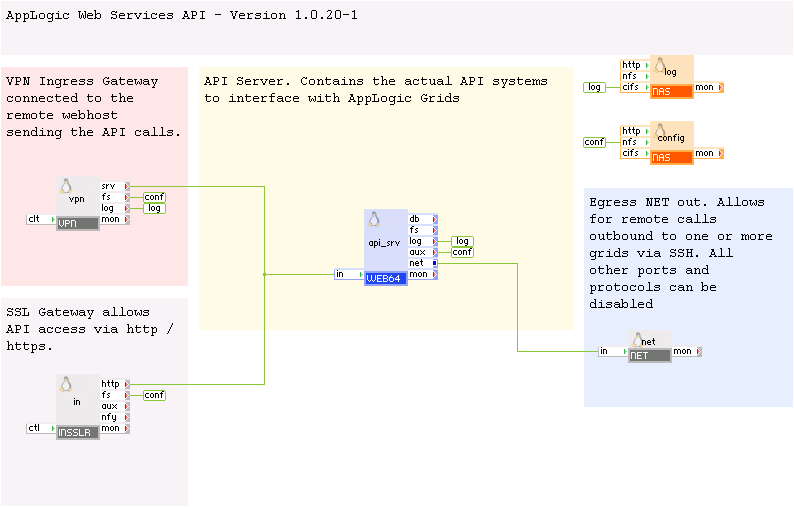
This section describes how to configure the WS_API application to start in one of the three different modes of operation.
To configure the WS_API application
app provision WS_API ws_api_instance --skipstart
vol manage ws_api_instance:conf
cd /mnt/vol/data ls vdcs.conf
This file consists of information necessary to access the grids that will be managed through the REST API.
vi vdcs.conf
vdcs
{
vdc controller_name : host = controller_ip or FQDN
{
location = "city, state, country"
latitude = latitude
longitude = longitude
}
# vdc controller_name : host = controller_ip or FQDN
# {
# location = "city, state, country"
# latitude = latitude
# longitude = longitude
# }
}
To generate the key pair:
ssh-keygen -t dsa -f /mnt/vol/data/gridkey When prompted to enter a password press enter. DO NOT ENTER A PASSWORD. chmod 600 /mnt/vol/data/gridkey* chown 99:99 /mnt/vol/data/gridkey*
cat /mnt/vol/data/gridkey.pub
user create api@domain.com pwd=- sshkey="ssh-dsa AAA.................xyz"
The user is created.
grid modify_acl local:user:api@domain.com=grid_administrator
Note: Other access levels can be used (see RBAC guide for more info) but be aware this will limit the commands the ws_api can run.
The application boundary can now be configured to work in either one of the three operating modes.
The WS_API application provides a web service interface to one or multiple grids through a Representational State Transfer (REST) based service. The HTTP access method enables simple HTTP based REST API calls.
Note: This mode should be used with extreme caution. There is no security check involved in this mode and anybody can create an API request without any authentication. Also, all the traffic between the client and the ws_api_instance application is in plaintext.
To configure the application in HTTP mode, set the http_mode property to http along with setting the mandatory properties to appropriate value. For example,
app config ws_api_instance usr_ip=usr-ip net_ip=net-ip netmask=netmask gateway=gateway dns1=dns1 dns2=dns2 http_mode=http
The application may now be started using the app start command or by using the "Start Application" button in the GUI.
The WS_API application provides a web service interface to one or multiple grids through a Representational State Transfer (REST) based service. The HTTPS access method enables secure HTTP based REST API calls.
To configure the application in HTTPS mode
Note: If opts is left blank then, a generic SSL certificate is generated on application start. The http_mode and the allowed_hosts property settings can be left set to their default values. For example,
app config ws_api_instance usr_ip=usr-ip net_ip=net-ip netmask=netmask gateway=gateway dns1=dns1 dns2=dns2 opts=ssl_country=Country,ssl_state=State,ssl_local=City,ssl_org_name=Organization,ssl_org_unit=Unit,ssl_common_name=Common Name,ssl_email_address=company@domain.com,ssl_export_pass=Passkey
The first time the application is started, a PEM formatted client key consisting of the client certificate and private key named api_client.pem and a PKCS12 formatted equivalent key for browsers named api_client.p14 is created in the /mnt/config/ssl_keys/keys/ directory of the conf volume. The api_client.p14 key file can be used for any browser based API access and the api_client.pem key for any non-browser based API access.
To generate any additional client certificates
The WS_API application provides a web service interface to one or multiple grids through a Representational State Transfer (REST) based service. The VPN access method enables HTTP requests to be sent through a secure VPN tunnel.
To configure the application in VPN mode
For example:
app config ws_api_instance usr_ip=usr-ip vpn_ip=vpn-ip net_ip=net-ip netmask=netmask gateway=gateway dns1=dns1 dns2=dns2 vpn_standby=0 in_standby=1
After the application starts, the VPN server appliance generates necessary server certificates and key files if these files are not already present.
[ws_api_instance:main.in_vpn appliance]# ./security.sh generate_client Generated client SSL cerfiticate and key file. ============================================== These files, with CA certificate file, should be copied to VPN server into /client/ subdirectory of data volume or fs-mounted volume. Path to client files (client.a1c65e2bae3d0b57) should be specified in auth_path property. Location of files: client certificate: /mnt/data/server/client.a1c65e2bae3d0b57.crt client key file: /mnt/data/server/client.a1c65e2bae3d0b57.key CA certificate file located at /mnt/data/server/ca.crt
The client certificate (for example, client.xxxxxxxxxxxxxxxx.crt) and key file (for example, client.xxxxxxxxxxxxxxxx.key) are generated in the client sub-directory and the CA certificate (ca.crt) is generated in server sub-directory of the conf volume.
Open source and third-party software used
The following open source third-party software is installed on the code volume.
|
Software |
Version |
Modified |
License |
Notes |
|
JSON |
2.15 |
No |
Artistic |
N/A |
|
IPC-Run |
0.80 |
No |
GPLv2 |
N/A |
|
XML-Simple |
2.18 |
No |
Artistic |
N/A |
|
Sort-Naturally |
1.02 |
No |
Artistic |
N/A |
|
Copyright © 2013 CA.
All rights reserved.
|
|