

Latest version: 1.0.4-1
|
At a Glance |
|
|
Catalog |
System |
|
Category |
Gateways |
|
User volumes |
no |
|
Min. memory |
96MB |
|
OS |
Linux |
|
Constraints |
no |
VPN2 is a Virtual Private Networking appliance that operates in IPv4 and IPv6 networks, designed to provide secure and reliable tunnels for inter-grid communications as well as remote access to applications and appliances. VPN2 can also operate without using VPN tunnels, in which case it functions as a combined cleartext IN/OUT gateway. VPN2 may also be used to seamlessly interconnect IPv4 and IPv6 grids. VPN2 is based on the OpenVPN, OpenSSH and Racoon open source software packages.
VPN has three basic modes of operation: server, client, and both.
VPN2 supports IPSec, shared secrets files, SSL certificates and ssh key files for authentication and encryption. A regular OpenVPN/OpenSSH client may be used on a remote workstation to connect to VPN2, which in turn provides secure access to the internal components of an application running on CA AppLogic. The VPN2 appliance supports the generation of shared secrets files, SSL certificates and ssh keys.
To remotely access a CA AppLogic application over a secure VPN tunnel using VPN2, the OpenVPN client-side software, or OpenSSH may be used on the client's machine (or some other compatible software).
Resources
|
Resource |
Minimum |
Maximum |
Default |
|
CPU |
0.1 |
16 |
0.2 |
|
Memory |
96 MB |
32 GB |
96MB |
|
Bandwidth |
1 Mbps |
2 Gbps |
250 Mbps |
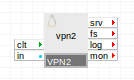
Terminals
|
Name |
Direction |
Protocol |
Description |
|
clt |
in |
any |
Common input for all incoming traffic to be directed through the in terminal when VPN is operating as a client. If VPN is configured to establish a tunnel on the in terminal, packets sent to clt are directed to an established tunnel, or dropped, if the tunnel is not up. |
|
in |
in,out |
any |
Receives all encrypted (incoming or outgoing) traffic for assigned IPs |
|
srv |
out |
any |
Common output for all outgoing traffic that is received through the in terminal when VPN is operating as a server. All traffic is filtered using the tcp_ports, udp_ports, ssh_ports and aux_protocols properties prior to be sent through the srv. |
|
fs |
out |
nfs |
Access to a network file system for shared file storage, providing read-write file access over NFS. This volume is mounted as /mnt/fs in the appliance's filesystem space and is used for storage of encryption keys and certificates. The connected server must have a read-write share named /mnt/data. Neither the data volume nor the NFS-mounted volume is required if VPN operates in cleartext mode. This terminal may be left unconnected if it is not used |
|
log |
out |
cifs |
Access to a CIFS-based network file system for storing access and error logs. The connected server must allow anonymous logins and have a read-write share named share. This terminal may be left unconnected if it is not used. |
|
mon |
out |
cce |
Used to send performance and resource usage statistics. May be left disconnected if not used. |
The in terminal is used for encrypted traffic (inbound or outbound.) This terminal is configured via the Interfaces tab of Application Configuration Editor.
Properties
General Properties
|
Property Name |
Type |
Description |
|
dns1 |
IP address |
Defines the primary DNS server to which VPN2 will forward DNS requests. If left empty, VPN2 will use the root DNS servers. Default: empty |
|
dns2 |
IP address |
Defines the backup DNS server to which VPN2 will forward DNS requests if the primary is not available. If left empty, VPN2 will not use a backup DNS server. Default: empty |
VPN Properties
|
Property Name |
Type |
Description |
|
mode |
String |
Mode of operation. Possible values are: server - VPN2 operates in server mode, accepting incoming traffic from established tunnels on the in terminal and sending it to the srv terminal. client - VPN2 operates in client mode, accepting incoming traffic on clt terminal and sending it into the established tunnel on the in terminal. both - VPN2 operates in both client and server modes. Default: server. |
|
tunnel |
String |
Type of the tunnel to establish. Possible values are: certificate - A VPN tunnel is established using SSL client and server certificates for authentication and encryption with OpenVPN. The server certificate is generated automatically if not present; the client certificate must be generated manually with the /appliance/security.sh script located on the VPN2 server and copied into the /client/ subdirectory on the data volume or nfs-mounted volume. This mode works with IPv4 and IPv6. shared secret - A VPN tunnel is established using a shared secrets file with OpenVPN. This file is automatically generated on the VPN2 server if not present, is located in the /server/ subdirectory of the data volume or nfs-mounted volume, and is named secret.key. This file must be copied on the client VPN2 appliance into the /client/ subdirectory. This mode works with IPv4 and IPv6. ssh key - An SSH tunnel is established using OpenSSH keyfiles for authentication. Keyfiles are generated with the /appliance/security.sh server-side script. The client keyfile must be copied into the /client/ subdirectory of the data volume of nfs-mounted storage. This mode works with IPv4 and IPv6. ipsec shared secret - IPSec tunnel is established between instances of VPN2. The first line of the file specified by the auth_path property is used as a shared key. This mode works only with IPv4. ipsec certificate - IPSec tunnel using certificates is established between instances of VPN2. The server certificate is generated automatically if not present or may be generated with the /appliance/security.sh script; the client certificate must be generated manually with the /appliance/security.sh script located on the VPN2 server and copied into the /client/ subdirectory on the data volume or nfs-mounted volume. This mode works only with IPv4. For the both mode of operation all certificates must be generated by the same appliance, and distributed with it's ca.crt certificate. cleartext - No tunnel is established; the VPN2 appliance operates as a combined IN/OUT gateway, accepting traffic on the clt terminal and forwarding it through the in terminal, and accepting traffic on the in terminal and forwarding it through the srv terminal. This mode works with IPv4 and IPv6. For IPv6 mode the remote_host property must contain the peer's address. Default: cleartext. |
|
auth_path |
String |
Authentication information for the tunnel. For the shared secret mode of operation, this is a relative path to the shared secrets file on the data volume (ex. "secret.key" for a "client/secret.key" file). For the certificate mode, this is a relative path, including the file name without extension, to the certificate/key file pair. For example, if the certificate files client1-2009.crt and client1-2009.key are located in the /client subdirectory of the data volume, "client1-2009" must be specified here. If the tunnel is cleartext, this property is ignored. If the tunnel is ssh key, this property indicates the path, including filename, to the ssh public (for VPN server) or private (for VPN client) key file (e.g. "/1/ssh.key" for a /client/1/ssh.key public key file). Default: empty |
|
log_level |
String |
VPN logging level. Possible values are: none - Nothing is logged. emerg - Logs only errors detected by VPN2. warn - Logs both warnings and errors. notice - Logs warnings, errors and notices. debug - Logs additional debug information in addition to warnings, notices and errors. Default: none if the log terminal is not connected; emerg if the log terminal is connected. |
Server Properties
|
Property Name |
Type |
Description |
|
allowed_hosts |
String |
List of hosts and/or subnets allowed to connect. Separate multiple entries with spaces or commas. Supported format example: 192.168.1.2 192.168.1.0/24 192.168.2.0/255.255.255.0 fc00:1234::12/64.
Default: 0.0.0.0/0 (all allowed, both IPv4 and IPv6) |
|
tcp_ports |
String |
Port numbers or port ranges to allow on thel srv terminal. Accepts a string of comma or space-separated values. Port ranges must be specified as lower_port:higher_port with colon or dash as a separator (e.g., 80,81,82:85 86-90). A special value of 0 means that all tcp ports are accepted.
Default: empty |
|
udp_ports |
String |
Same as tcp_ports, but for UDP protocol.
Default: empty |
|
aux_protocols |
String |
A string of comma or space-separated additional IP Protocol numbers to allow (e.g., 6 for TCP, 47 for GRE). Separate protocols may be specified by their names (ex. 'gre' instead of '47'). See protocol-numbers for assignment.
Default: empty (disabled) |
Client Properties
|
Property Name |
Type |
Description |
|
remote_host |
String |
Defines the remote host to forward all traffic to. This can be the DNS name of the host or its IPv4 or IPv6 address in "dots" notation. This property is mandatory. Default: empty |
|
dns_poll |
Integer |
The poll interval, in seconds, that VPN2 will use when checking the mapping of the DNS name of remote_host to IP address (used only if remote_host is specified as a DNS name). Set to 0 to disable polling and not try to detect changes. Default: 3600 seconds (1 hour). |
|
ssh_ports |
String |
A client-side property for ssh key mode, that specifies what tcp ports to forward to the VPN2 server. Port ranges are not supported, ports may be divided by spaces or commas. Default: empty |
Volumes
|
Name |
Description |
|
data |
A read-write data volume (placeholder) containing config files and certificate files. This volume Is not required if the fs terminal is connected. If fs is connected, and a data volume is supplied, VPN2 fails to start and logs an error message. All files that are necessary for VPN2 server operation are stored in the /server/ subdirectory of the data storage. All files that are necessary for VPN2 client operation, are stored in the /client/ subdirectory. |
Custom Counters
The VPN2 appliance reports the following custom counters through the mon terminal.
|
Counter Name |
Description |
|
server_bytes_in |
Total bytes received by VPN2. |
|
server_bytes_out |
Total bytes sent by VPN2. |
|
client_bytes_in |
Total bytes sent by VPN2. |
|
client_bytes_out |
Total bytes sent to client tunnels. |
|
client_bytes_out |
Number of clients connected to VPN2. |
Performance
Two test applications were residing on the same CA AppLogic grid. 100mbit bandwidth was assigned to both VPN2 appliances (client and server), and to server and client appliances. Multiple object, each 1Mbyte in size, were fetched, 10 objects in parallel, for 60 seconds.
|
Mode |
Bandwidth,Mbit/second |
Object size |
Requests/second |
Transfer rate, MBytes/second |
|
Certificate |
100 |
1MB |
12.5667 |
12.56 |
|
Shared secret |
100 |
1MB |
12.5166 |
12.51 |
|
SSH key |
100 |
1MB |
12.7667 |
12.76 |
|
Cleartext |
100 |
1MB |
13.0329 |
12.76 |
Error Messages
In case of appliance startup failure, the following errors may be logged to the system log:
|
Error Message |
Description |
|
Failed to mount the data volume |
VPN2 failed to mount the data volume. Verify that the volume is formatted and available. |
|
Failed to generate server_key |
VPN2 failed to generate shared secrets file. Probably the data volume is too small, or mounted read-only. |
|
Failed to launch OpenVPN server |
VPN2 failed to launch OpenVPN server. Please contact 3Tera support. |
|
Failed to generate certificates. |
VPN2 failed to create Certification Authority and generate necessary certificated for certificate server mode of operation. Probably the data volume is too small, or mounted read-only. |
|
Failed to generate DH file. |
VPN2 failed to generate Diffie-Hellman key file. Probably the data volume is too small, or mounted read-only. |
|
Secrets file client_auth does not exist |
File client_auth, specified in the auth property, does not exist. Verify the path and name of the file. |
|
Remote server address is empty for |
Remote VPN2 server address is empty for tunnel X. |
|
Failed to launch OpenVPN for clientX tunnel |
VPN2 failed to launch OpenVPN software for client tunnel X. Probably some properties or key files are invalid. |
|
Certificate file client_auth.crt does not exist |
VPN2 failed to locate a certificate file. Invalid path or file name specified in auth property for the certificate client mode of operation. |
|
Key file client_auth.key does not exist |
VPN2 failed to locate a key file. Invalid path or file name specified in auth property for the certificate client mode of operation |
|
Certification Authority certificate ca_cert is missing |
VPN2 failed to locate Certification Authority certificate. It should be located in /CA/ca.crt file on the data volume. |
Types of tunnels
Cleartext
This mode supports a "single server - multiple clients" scenario, allowing access to the VPN2 server from multiple locations. In this mode VPN tunnels are not established, and a data store is not required (neither a data volume nor a NAS appliance connected to the fs terminal). This mode operates in IPv4 and IPv6.
On the server VPN2 appliance, traffic received on the in terminal is filtered through the tcp_ports, udp_ports, aux_protocols properties and forwarded to the srv terminal.
On the client VPN2 appliance, all traffic received on the clt terminal is forwarded to the remote VPN2 server, specified in the remote_host property.
Properties that must be configured on the server side: mode, tunnel, allowed_hosts, tcp_ports, udp_ports, aux_protocols.
Properties that must be configured on the client side: mode, tunnel, remote_host.
Server-side property remote_host must be configured with client's address if IPv6 mode is in use.
Certificate
This mode supports a "single server - multiple clients" scenario, allowing access to the VPN2 server from multiple locations. A data store is required (either a data volume or a NAS appliance connected to the fs terminal). This mode operates in both IPv4 and IPv6.
Upon start, the server appliance generates necessary certificates and key files if these files are not already present. These files may be re-generated with the security.sh script, located in the /appliance/ directory. Prior to configuring any VPN2 clients, certificates must be generated for them. A user may login into the running VPN2 server appliance and generate a client keypair as follows:
grid> comp login VPN2-1:main.VPN2
CentOS release 6 (Final)
[VPN-1:main.VPN ~]# /appliance/security.sh generate_client
Generated client SSL cerfiticate and key file.
==============================================
These files, with CA certificate file, should be copied to VPN2 server into
/client/ subdirectory of data volume or fs-mounted volume.
Path to client files (client.829de5afcac564b3) should be specified in auth_path property.
Location of files:
client certificate: /mnt/fs/server/client.829de5afcac564b3.crt
client key file: /mnt/fs/server/client.829de5afcac564b3.key
CA certificate file located at /mnt/fs/server/ca.crt
The client certificate and key file must be copied to the client VPN2 appliance to the /client/ subdirectory of the data store, and the auth_path set to the appropriate value, "client.829de5afcac564b3" in this case. The CA certificate from the VPN2 server (/mnt/fs/server/ca.crt) must be copied to the /client/ subdirectory on the client appliance as well, and named "ca.crt". Every client VPN2 appliance should have it's own certificate.
On the server VPN2 appliance, traffic received on the in terminal is decrypted, filtered through the tcp_ports, udp_ports, aux_protocols properties and forwarded to the srv terminal.
On the client VPN2 appliance, all traffic received on the clt terminal is encrypted and forwarded to the remote VPN2 server, specified in the remote_host property.
Properties that must be configured on the server side: mode, tunnel, allowed_hosts, tcp_ports, udp_ports, aux_protocols.
Properties that must be configured on the client side: mode, tunnel, remote_host, auth_path.
Shared secrets file
This mode supports only the "single server - single client" scenario, allowing access to the VPN2 server from only single client at one time. A data store is required (either a data volume or a NAS appliance connected to the fs terminal). This mode operates in both IPv4 and IPv6.
Upon the start, the server appliance generates a shared secrets file "/server/secret.key", if this file is not already present. This file may be re-generated with the security.sh script, located in the /appliance/ directory. Prior to configuring any VPN2 clients, this shared secrets file must be copied to it's data store into the /client/ subdirectory. To generate a new shared secrets file, a user may login into the running VPN2 server appliance and issue the following command:
[VPN2-1:main.VPN2 server]# /appliance/security.sh generate_secret
Generated OpenVPN shared secrets file.
======================================
This file should be copied to VPN2 server into /server/ subdirectory of data volume or fs-mounted volume,
and to the VPN2 client into /client/ subdirectory of data volume or fs-mounted volume.
Path to it should be specified in auth_path property of the VPN2 client.
Location of file: /mnt/fs/server/secret.key
A freshly-generated secrets file overwrites the old one, if it existed. This shared secrets file "/mnt/fs/server/secret.key" must be copied to the client VPN2 appliance into /client/ subdirectory of the data store, and auth_path property set to the correct value, "secret.key" in this case. Multiple client VPN2 appliances may be configured, but only one can be connected at any time.
On the server VPN2 appliance, traffic received on the in terminal is decrypted, filtered through the tcp_ports, udp_ports, aux_protocols properties and forwarded to the srv terminal.
On the client VPN2 appliance, all traffic received on the clt terminal is encrypted and forwarded to the remote VPN2 server, specified in the remote_host property.
Properties that must be configured on the server side: mode, tunnel, allowed_hosts, tcp_ports, udp_ports, aux_protocols.
Properties that must be configured on the client side: mode, tunnel, remote_host, auth_path.
Ssh key
This mode supports a "single server - multiple clients" scenario, allowing access to the VPN2 server from multiple locations. A data store is required (either a data volume or a NAS appliance connected to the fs terminal). Only tcp traffic may be tunneled through the ssh tunnel, so only tcp_ports property is used on the server side. Port ranges are not supported - every ports that should be forwarded must be specified explicitly in ssh_ports client-side property. This mode operates in both IPv4 and IPv6.
VPN2 server generates the default ssh keypair upon start; default keys are located at: server key (public key): server/ssh-server.pub client key (private key): server/ssh-client.key Additional keys may be generated manually using the security.sh script:
[VPN2-1:main.VPN2 ~]# /appliance/security.sh generate_ssh
Generated SSH keypair.
======================
Public key should be copied to VPN2 server into /server/ subdirectory of data volume or fs-mounted volume.
Private key should be copied to VPN2 client into /client/ subdirectory of data volume or fs-mounted volume.
Path to key files should be specified in auth_path property on both VPN2 client and server.
Location of files:
Public key: /mnt/fs/server/ssh.11179ebbfa3f6852.pub
Private key: /mnt/fs/server/ssh.11179ebbfa3f6852.key
The public key should be copied to the VPN2 server into the /server/ subdirectory; the private key should be copied to the client into the /client/ subdirectory. The auth_path property should be set on both client and server. If auth_path is empty on the server, the default SSH key is used.
On the server VPN2 appliance, traffic received on the in terminal is decrypted, filtered through the ssh_ports property and forwarded to the srv terminal. Only tcp port forwarding is supported. The auth_path property defines the public ssh key to use. When the appliance is working in both client and server mode, both public and private keys should be named the same, and located in /server/ and /client/ subdirectories. The ssh_ports property should be configured on both server and client in the same way.
On the client VPN2 appliance, all traffic received on the clt terminal is encrypted and forwarded to the remote VPN2 server, specified in the remote_host property.
Properties that must be configured on the server side: mode, tunnel, allowed_hosts, auth_path, tcp_ports.
Properties that must be configured on the client side: mode, tunnel, remote_host, auth_path, ssh_ports.
Note: SSH server-server mode. Two VPN2 appliances may both be configured in both mode and connect to each other. In order to use this mode, appliances must be configured in a special way:
Assuming you have 2 appliances named VPN21 and VPN22:
IPSec certificate
This mode supports a "single server - multiple clients" scenario, allowing access to the VPN2 server from multiple locations. A data store is required (either a data volume or a NAS appliance connected to the fs terminal). This mode operates only in IPv4.
Upon start, the server appliance generates necessary certificates and key files if these files are not already present. These files may be re-generated with the security.sh script, located in the /appliance/ directory. Prior to configuring any VPN2 clients, certificates must be generated for them. A user may login into the running VPN2 server appliance and generate a client keypair as follows:
grid> comp login VPN2-1:main.VPN2
CentOS release 6 (Final)
[VPN2-1:main.VPN2 ~]# /appliance/security.sh generate_client
Generated client SSL cerfiticate and key file.
==============================================
These files, with CA certificate file, should be copied to VPN2 server into
/client/ subdirectory of data volume or fs-mounted volume.
Path to client files (client.829de5afcac564b3) should be specified in auth_path property.
Location of files:
client certificate: /mnt/fs/server/client.829de5afcac564b3.crt
client key file: /mnt/fs/server/client.829de5afcac564b3.key
CA certificate file located at /mnt/fs/server/ca.crt
The client certificate and key file must be copied to the client VPN2 appliance to the /client/ subdirectory of the data store, and the auth_path set to the appropriate value, "client.829de5afcac564b3" in this case. The CA certificate from the VPN2 server (/mnt/fs/server/ca.crt) must be copied to the /client/ subdirectory on the client appliance as well, and named "ca.crt". Every client VPN2 appliance should have it's own certificate.
Important! An exception exist when VPN2 is used in both mode. In this case all certificates, client and server ones, must be generated by the same VPN2 instance, and distributed together with it's ca.crt certificate to other instances.
On the server VPN2 appliance, traffic received on the in terminal is decrypted, filtered through the tcp_ports, udp_ports, aux_protocols properties and forwarded to the srv terminal.
On the client VPN2 appliance, all traffic received on the clt terminal is encrypted and forwarded to the remote VPN2 server, specified in the remote_host property.
Properties that must be configured on the server side: mode, tunnel, allowed_hosts, tcp_ports, udp_ports, aux_protocols.
Properties that must be configured on the client side: mode, tunnel, remote_host, auth_path.
|
Copyright © 2013 CA Technologies.
All rights reserved.
|
|