

A user that attempts to access the web application protected by CA Strong Authentication is authenticated using any of the out-of-the-box credentials.
In all the authentication mechanisms, the client is provided with an authentication token after every successful authentication. The authentication token is further used to prove that the client is already authenticated to the server. The authentication token is valid only for a certain interval, after which the client has to re-authenticate to the server.
All password type credentials namely, password, OTP/Activation Code, CA Auth ID OTP, and OATH OTP Token are based on the single-step authentication model, which means the credentials are passed by the client to the user and the server verifies the user credentials.
The following figure illustrates the typical authentication flow.
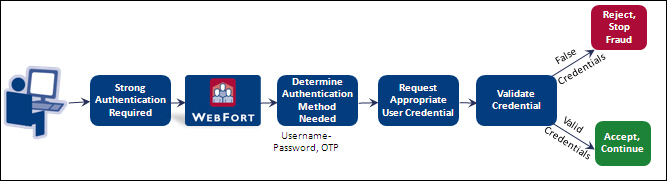
However, CA Auth ID and QnA are based on the challenge-response authentication model. These authentication mechanisms include multiple steps to authenticate users.
|
Copyright © 2014 CA Technologies.
All rights reserved.
|
|