

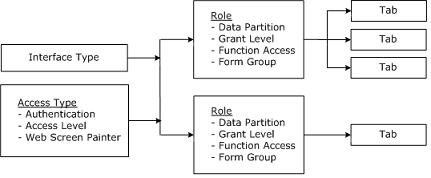
Access types and roles are the primary components you use to control CA SDM security.
The following diagram shows an overview of how roles interrelate with other system objects to provide role-based security.
Note: For more information about other aspects security, see Security.
|
Copyright © 2013 CA.
All rights reserved.
|
|