When a user attempts to access a protected network resource, the Policy Server uses the authentication scheme associated with the resource’s realm to to determine how to identify the user. The authentication scheme specifies the credentials that the user must supply for authentication, as well as the method used by the Policy Server to validate the user’s identity.
You can use the Policy Server User Interface to configure authentication schemes and assign the schemes to realms. The following diagram illustrates how an authentication scheme is called when a user attempts to access a protected resource.
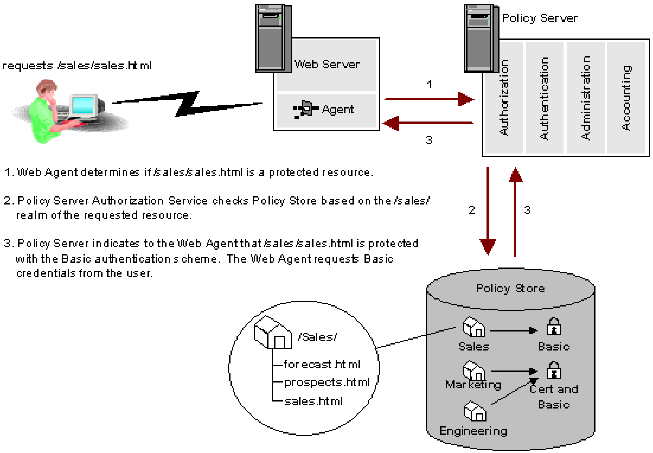
In the example above, the user requests the protected resource sales.html from the /Sales/ realm. This realm requires Basic authentication. The Policy Server informs the Web Agent that the resource is protected and requests Basic credentials from the user via the Web Agent, which prompts the user for a user name and password.
| Copyright © 2011 CA. All rights reserved. | Email CA Technologies about this topic |