Federation Security Services Guide › Federation Security Services Overview › Solutions for Federation Use Cases › Solution 9: SAML 2.0 User Authorization Based on a User Attribute
Solution 9: SAML 2.0 User Authorization Based on a User Attribute
Solution 9 shows how SiteMinder Federation Security Services can be deployed at sitemindercars.com and exampleair.com to solve Use Case 9: SAML 2.0 User Authorization Based on a User Attribute.
Note: This solution is only for SAML 2.0.
Note: The SPS federation gateway can replace the Web Agent and Web Agent Option Pack to provide the SiteMinder Federation Web Services application functions. For information about installing and configuring the SPS federation gateway, see the CA SiteMinder Secure Proxy Server Administration Guide.
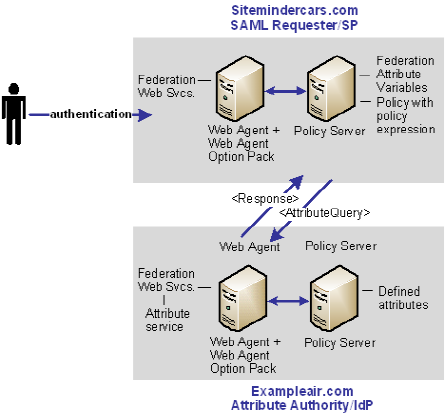
SiteMinder is deployed at both sites by installing the Web Agent with the Web Agent Option Pack on a Web server and the Policy Server with federation security services on another machine. The installations are the same for both sites.
In this solution, sitemindercars.com is a Service Provider acting as a SAML Requester. When a customer logs on at this site, the sequence of events is as follows:
- The user logs in to sitemindercars.com and the Web Agent provides the authentication.
- When the user clicks a link to rent a car, the Web Agent first makes a request to the Policy Server at the local site.
- The Policy Server evaluates the policy expression and determines that there are unresolved federation attribute variables. The Policy Server tries to resolve the variable by looking up the user in the user directory associated with the policy protecting the requested URL.
- The local Policy Server cannot resolve the user attribute variable. It locates the NameID configuration for the Attribute Authority, Exampleair.com. This is the Attribute Authority where the <AttributeQuery> will be sent.
- The Policy Server sends an <AttributeQuery> containing the NameID and the frequent flyer attribute to the Exampleair.com, which is acting as the Attribute Authority.
- Exampleair.com returns a response to sitemindercars.com that contains an attribute assertion which includes the requested attribute.
- The SAML Requester resolves the variables and evaluates the policy expression, returning authorization status to the Web Agent.
- The Web Agent allows access to the appropriate resource.
