To test single sign-on in an FSS-to-FSS network, you can use the web pages included with the FSS sample application, provided you have previously run the FSS sample application script. If you do not run the FSS sample application, you have to use your own web pages to test single sign-on.
The sample application web pages are located in the following two folders.
policy_server_home/samples/federation/content/idpsample
policy_server_home/samples/federation/content/spsample
Specifies the installed location of the SiteMinder Policy Server.
Important! If you have run the sample application, the idpsample and spsample folders are automatically copied into your web server's document root directory.
If you choose to use your own html page to test SP-initiated single sign-on, the HTML page must contain a hard-coded link to the AuthnRequest service. For this deployment, the sample link for POST binding is:
http://www.sp.demo:81/affwebservices/public/saml2authnrequest?ProviderID=idp.demo
The AuthnRequest Service redirects the user to the Identity Provider specified in the link to retrieve the user's authentication context. After the Identity Provider authenticates the user and establishes a session, it directs the user back to the target resource at the Service Provider.
Note: The ProviderID in the Authnrequest link must match the IdP ID field value specified by the SAML authentication scheme at the SP. The IdP ID field is located on the Scheme Setup tab of the Authentication Scheme Properties dialog.
After running the sample application, you should can test single sign-on.
To test federated single sign-on
http://www.idp.demo:server_port/idpsample/index.jsp
http://www.sp.demo:server_port/spsample/index.jsp
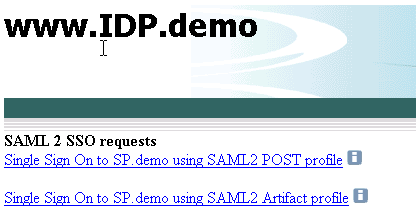
The following figure is the IdP.demo home page:
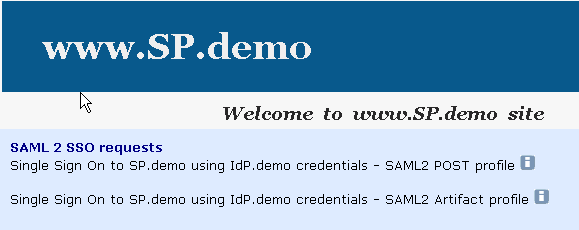
The following figure is the SP.demo home page:
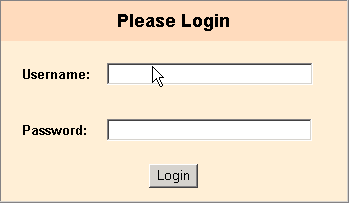
A login challenge like the following is presented:
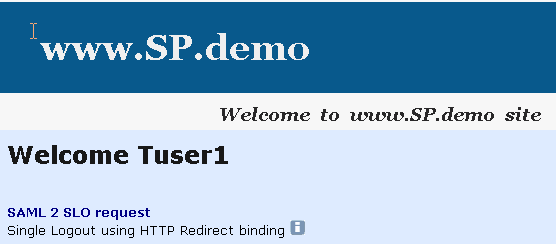
If single sign-on is successful, you should see the following welcome page:
| Copyright © 2010 CA. All rights reserved. | Email CA about this topic |