Policy Server Guides › Policy Server Configuration Guide › Impersonation › Impersonation Process
Impersonation Process
The process of impersonating another user consists of the following:
- A privileged user (impersonator) establishes a SiteMinder session by accessing a resource protected by SiteMinder. This can be the Administrative UI or some other application or resource protected by a SiteMinder policy.
- The impersonator, using the currently established identity, accesses a form which allows the impersonator to specify the user to be impersonated (impersonatee). The impersonator does not present the credentials of the impersonatee. The form is an .fcc file with special logic to enable the impersonated session.
- The impersonator submits information about the impersonatee.
The Policy Server determines whether or not the impersonator may be impersonated using a series of policies.
- Determines whether or not the impersonator has sufficient rights to impersonate the impersonatee.
- Uses the impersonator's established session when granting the impersonator access as the impersonatee.
- Audits all impersonator activity.
To begin an impersonated session, an impersonator accesses an .fcc file directly that has a target that points to a resource in the realm protected by the impersonation authentication scheme.
The following diagram shows an example of impersonation where a customer service representative (CSR) accesses an .fcc file directly to begin an impersonation session.
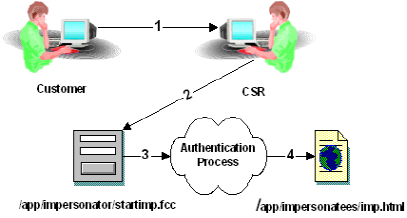
- A customer with a problem calls his CSR. The CSR determines that the best way to solve the customer's problem is to impersonate the customer.
- The CSR accesses the impersonation start page which in this case is named "/app/impersonators/startimp.fcc" to begin the impersonation process. The Forms Credential Collector (FCC) presents a form to the CSR. The CSR provides the name of the customer to be impersonated, and possibly other attributes for disambiguation. Within the .fcc file are directives (not shown) that collect the session specification of the CSR for use by the authentication scheme. The impersonation authentication scheme is invoked on the Policy Server because the target of the FCC resides in a SiteMinder realm that is protected by the impersonation authentication scheme.
- The Policy Server takes the information gathered by the FCC and uses it to determine if the customer to be impersonated can be found in any of the configured user directories. If found, the Policy Server determines if the CSR may impersonate the customer, and if the customer may be impersonated. If both are allowed, the Policy Server authenticates the impersonator and the CSR acts as the customer for the duration of the impersonated session.
- Finally, the Policy Server directs the CSR (impersonating the Customer) to the target of the FCC.
