Policy Server Guides › Policy Server Configuration Guide › Implementing Policy-based Security › Security Model Implementation
Security Model Implementation
To implement a security model that best meets the needs of your organization, you may create security policies using information gathered in the design phases shown and described below.
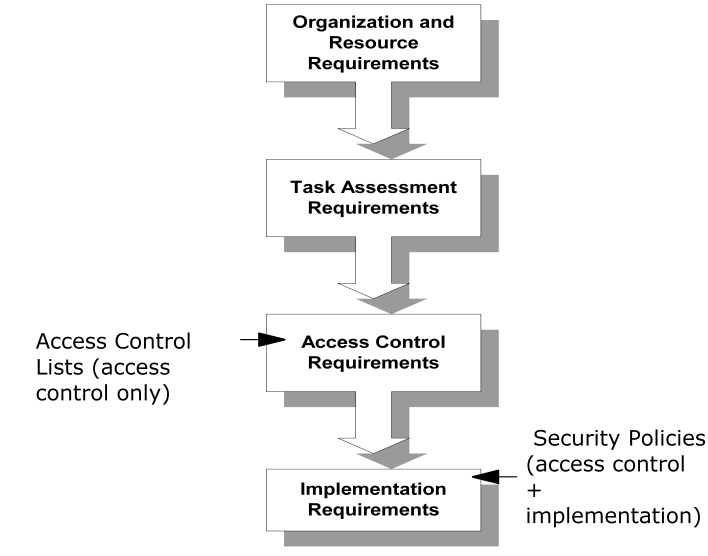
- Organization and resource requirements—set the basic objective of the security model and identify the resources.
- Task assessment requirements—identify users and roles, and link the roles to tasks.
- Access control requirements—establish access requirements for users based on their role requirements.
Authorization models based only on access control lists (ACLs) end at this point.
- Implementation requirements—define how the access is implemented (in terms of how users are tracked and how content is personalized for users) and how user sessions are managed.
Authorization models based on SiteMinder security policies incorporate both access control and implementation models.
