Policy Server Guides › Policy Server Configuration Guide › Impersonation › Policy Server Objects for Impersonation › Configure Policies for Impersonation
Configure Policies for Impersonation
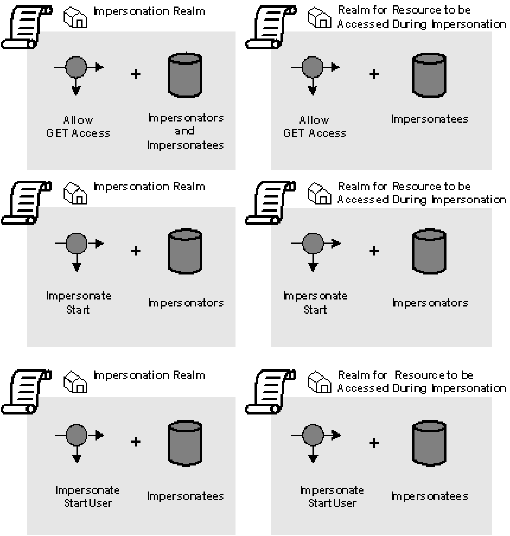
In order for impersonation to function correctly, multiple policies must be configured.
For the resource that initiates impersonation:
- Access control policy for both impersonators and impersonatees. For example, a policy that includes a GET access rule for both impersonators and impersonatees.
- Impersonation policy that includes an ImpersonationStart rule and impersonators.
- Impersonation policy that includes an ImpersonationStartUser rule and impersonatees.
For the resource to be accessed by the impersonator:
- Access control policy for impersonatees. For example, a policy that includes a GET access rule for impersonatees.
- Impersonation policy that includes an ImpersonationStart rule and impersonators.
- Impersonation policy that includes an ImpersonationStartUser rule and impersonatees.
Note: Policies must be in place for each resource that may be accessed by an impersonator.
The following figure shows the minimum policies required for an impersonator to access a resource: