User disambiguation is the process of locating a unique user in a user directory. There are two methods of locating users in a user directory. You can locate users by
The Policy Server uses information you supply in the User Lookup group box of the User Directory pane, and a user-supplied value, such as login name, to locate a user.
User Lookup by DN
You construct a user lookup by DN from the User Directory pane in the User Lookup group box of the LDAP Settings area. You concatenate the value specified in the User Lookup Start field, the username as specified by the user during login, and the value specified in the User Lookup End field.
The resulting DN has the following format:
<value in the User Lookup Start field>, <username>, <value in the User Lookup End field>
The following illustrates an LDAP Directory Information Tree (DIT) example:
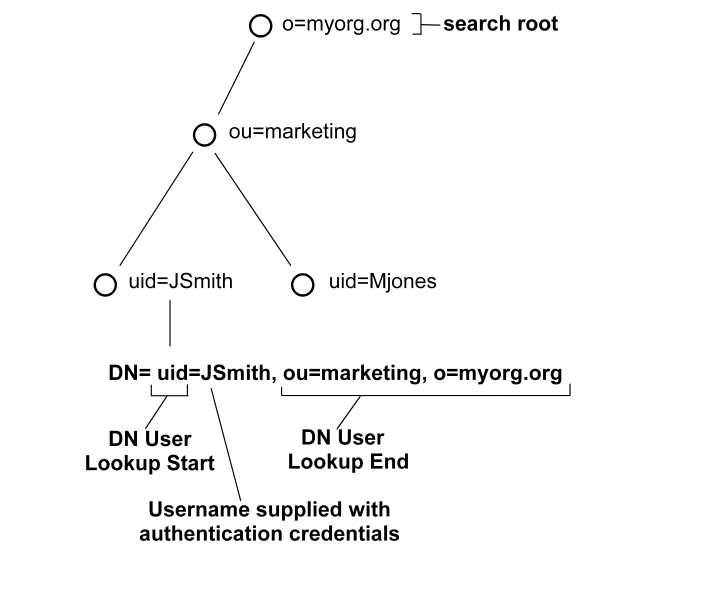
In the previous diagram, the LDAP DIT design requires a DN to be of the form uid=JSmith,ou=marketing,o=myorg.org.
Only the unique part, JSmith, must be specified in the credentials when the user logs in.
User Lookup via a Search Expression
An LDAP directory server may contain numerous users in complicated DITs, and it may not be practical to create a large number of user directory connections. Your organization may have hundreds of organizational units and you may want to avoid having end users log in with detailed string representations. Instead, one user directory connection pointing to a common root can be created with the User DN Lookup Start and User DN Lookup End properties defining an LDAP search expression. The result of the search expression is a list of user DNs for the Policy Server to try during authentication.
Example: Search expressions for user DN lookups
To locate a user across many organizational units, define the User Lookup Start property as (&(objectclass=inetOrgPerson)(uid= and define the User Lookup End property as )). Only the unique part, the uid value, must be specified in the credentials. In the section of the User Directory Dialog shown above, these values replace the values contained in the LDAP User DN Lookup group box.
Note: An InetOrgPerson is a common object class used in LDAP directory deployments.
See the following figure for the type of LDAP DIT where invoking a search expression is useful:
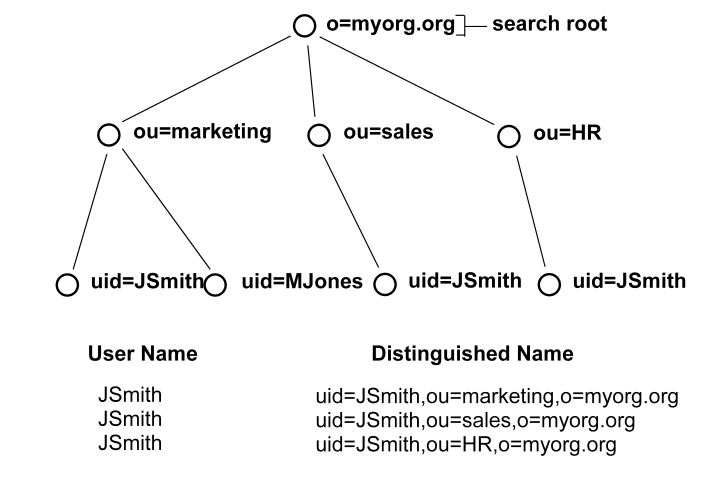
In this case, if JSmith from ou=sales wants to access a resource, JSmith can authenticate using only his or her name for credentials (as opposed to an entire DN string). By placing the uid= attribute between the User DN Lookup Start and User DN Lookup End fields with the search expressions in the corresponding fields, the Policy Server will find all DNs that match the LDAP query (&(objectclass=inetOrgPerson)(uid=JSmith)).
The Policy Server then has a list of DNs to choose from in giving access to the protected resource. Assuming the resource can only be accessed by the JSmith of ou=sales, the username/password for the DN uid=JSmith,ou=sales,o=myorg.org will be the one that is authenticated.
As you work with LDAP directory connections in the Policy Server, you may need to specify filters for LDAP search expressions. The following table provides a brief description of some common LDAP search filters.
|
Search Filter |
Format |
Description |
|---|---|---|
|
Equality |
attribute=value For example, to find a user whose user ID is jsmith, the search filter is uid=jsmith. |
This filter finds a specific value for an attribute in an LDAP directory. |
|
String
|
attribute=*value, OR For example, uid=*smith matches all values that end in smith, such as jsmith, msmith, etc. A value of uid=*smith* matches jsmith, msmith, and bsmithe. |
LDAP search filters support wild cards, which allow you to search for an attribute value based on a partial string. To find all of the values that match a partial string, use the wildcard character (*).
|
|
Greater than or equal to |
attribute>=value For example, to find all of the users in a directory who are age 21 or over, part of the search filter would be age>=21. |
This filter finds values that are greater than or equal to the specified value. |
|
Less than or equal to
|
attribute<=value For example, to find all of the users in a directory who are age 21 or younger, part of the search filter would be age<=21. |
This filter finds values that are less than or equal to the specified value.
|
|
Greater than |
(!(attribute<=value)) For example, to find all of the users in a directory who are older than 21, part of the search filter would be (!(age<=21)). |
LDAP does not support greater than expressions. In order to filter LDAP attribute values by greater than, you must use the Negation operator (!) in conjunction with a greater than or equal to expression. |
|
Less than |
(!(attribute>=value)) For example, to find all of the users in a directory whose age is less than 21, part of the search filter would be (!(age>=21)). |
LDAP does not support less than expressions. In order to filter LDAP attribute values by less than, you must use the Negation operator (!) in conjunction with less than or equal to expression. |
|
Approximate |
attribute~=value For example, the filter uid~=smith may return the values smithe and smitt. |
This filter returns values that are similar to the value specified in the filter. |
|
Presence |
attribute=* For example, email=* returns all users who have an email address. |
This filter determines if an attribute is present. |
|
Complex And (&) Or (|) Not (!) |
Intersection of Filter1 and Filter2: Union of Filter1 and Filter2: Satisfies Filter1, but not Filter2: Note You must use parentheses to enclose the complex filter and each filter in the complex filter. For example, if you want to find all users whose User ID begins with the letter s and who are over 21 years old, you could use a filter of (&(uid=s*)(!(age<=21))).
|
Creates complex search filters. |
Objectclass Searches
Each entry in an LDAP table has at least one objectclass attribute. You can use a presence filter in conjunction with the objectclass attribute to build filters for searching your LDAP user directories. In SiteMinder environments, the objectclass attribute is most useful in the following cases:
To retrieve all entries one level below a directory entry, specify a search scope of One Level, and use a search filter of (objectclass=*). Since all LDAP directory entries have at least one objectclass attribute, the search filter returns a complete list of the entries below the root.
To retrieve all entries in the branches below a directory entry, specify a search scope of Subtree, and use a search filter of (objectclass=*). The search filter returns a complete list of the entries in the entire subtree.
Filtered Characters in User IDs
SiteMinder provides LDAP search filter checking functionality that parses LDAP search filters to ensure that they comply with the LDAP standard (RFC).
All user login IDs are filtered for "(", ")", "\" characters by default before being checked against an LDAP user store. To disable this check, set the following EnableSearchFilterCheck registry value to 0:
HKEY_LOCAL_MACHINE\SOFTWARE\Netegrity\Siteminder\Ds\LDAPProvider\EnableSearchFilterCheck
Important! By disabling this check, you may expose your system to attack, and should not allow user IDs using these characters.
| Copyright © 2010 CA. All rights reserved. | Email CA about this topic |