Federation Security Services Guide › Use an Attribute Authority to Authorize Users › Flow Diagram for Authorizing a User with User Attributes
Flow Diagram for Authorizing a User with User Attributes
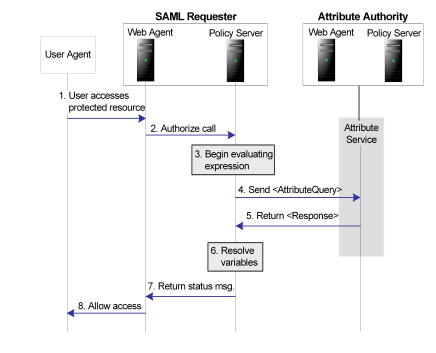
The following flow diagram shows the authorization process with an Attribute Authority.
Note: The SPS federation gateway can replace the Web Agent and Web Agent Option Pack to provide the SiteMinder Federation Web Services application functions. For information about installing and configuring the SPS federation gateway, see the CA SiteMinder Secure Proxy Server Administration Guide.
The sequence of a user attribute request is as follows:
- A user accesses a protected resource. The user might be logged in locally or may have authenticated via a SAML assertion.
- The Web Agent at the SAML Requester makes a call to the local Policy Server determine if the user is authorized to access the resource. The policy that protects the resource uses a policy expression for authorization with a federated attribute variable.
- The Policy Server tries to resolve these variables but cannot. The Policy Server looks the user up in the local user store to obtain the user's NameID.
- An attribute query is sent to the AttributeService URL at the Attribute Authority. The AttributeQuery contains the users NameID and the requested attributes.
- The Attribute Authority returns a SAML response containing an assertion with the requested attributes.
- The SAML Requester completes the resolution of variables and then evaluates the policy expression.
- An authorization status message is returned to the Web Agent.
- Depending on the authorization status, the Web Agent allows or denies access to the requested resource.
