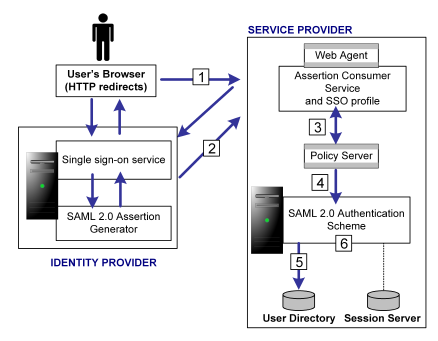
The following illustration shows how the SAML 2.0 authentication scheme processes requests.
Note: The SPS federation gateway can replace the Web Agent and Web Agent Option Pack to provide the SiteMinder Federation Web Services application functions. For information about installing and configuring the SPS federation gateway, see the CA SiteMinder Secure Proxy Server Administration Guide.
The functional flow for authentication is as follows:
In the case of the HTTP-POST binding, the response contains the assertion. For the HTTP-Artifact binding, the response contains a SAML artifact.
If the artifact binding is being used, the Assertion Consumer Service sends the artifact to the Identity Provider to obtain a response that contains the actual assertion. The Assertion Consumer Service sends the response with the assertion as credentials to the Policy Server.
Note: For the POST binding, a signature is required and there must be certificate lookup information supplied. If a signature is not present, authentication fails. However, for the Artifact binding, a signed assertion is optional because the assertion response is obtained over a secure channel between the Service Provider and Identity Provider.
If Single Logout is enabled, the user is redirected by the SLO servlet to a No Access URL.
| Copyright © 2010 CA. All rights reserved. | Email CA about this topic |