Before your environment can operate in FIPS-only mode, you must:
The following figure illustrates a sample r12.1 SP3 environment and details:
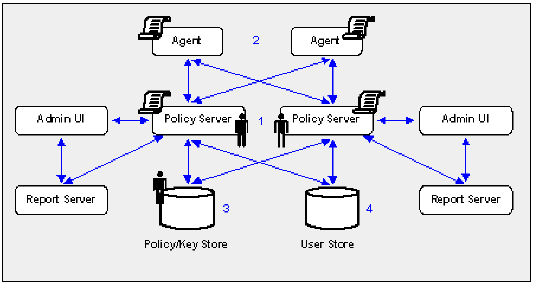
Important! If you have configured a separate database for a key store, audit logs, token data, or a session server, these passwords are encrypted using algorithms that are not FIPS compliant. Re-encrypt these passwords before configuring the environment for FIPS-only mode.
Note: This is the password for the default SOA Security Manager administrator account. This account is used for all administrative tasks that do not require direct access to the Administrative UI. This is not the password for the Administrative UI administrator account with Super User privileges.
The shared secrets that the Policy Servers and Agents use to establish encrypted communication channels are encrypted using algorithms that are not FIPS compliant. Re-encrypt the shared secrets before configuring the environment for FIPS-only mode.
Note: The previous figure depicts a single database instance as a policy/key store. Your environment may use separate database instances for individual policy and key stores.
Sensitive data stored in a policy store or policy and key stores is encrypted using algorithms that are not FIPS compliant. Re-encrypt the keys and sensitive policy store data before configuring the environment for FIPS-only mode.
| Copyright © 2011 CA. All rights reserved. | Email CA Technologies about this topic |