Complex sets of resources must be logically grouped so that security policies can be created. The basic SOA Security Manager groupings for resources are realms.
A realm is a cluster of resources within a policy domain grouped according to security requirements. A realm is usually defined for resources that reside in a common location on your network. For example, web services that process incoming purchase orders and are bound to URLs in an /Orders directory or accessible by an Orders JMS queue might be configured as a realm in a policy domain managed by an administrator in a company’s order fulfillment organization. The realm also specifies the authentication scheme to be used. Typically, you should create a realm for each web service (as defined by a WSDL port element).
Web service resources are identified in the realm according to whether they will be accessed by HTTP(S) or JMS transports as follows:
The contents of a realm are protected by SOA Agents. When web service clients request resources within a realm, the associated SOA Agent handles authentication and authorization of the user associated with the request. The realm determines the method of authentication.
The following diagram shows the contents of two realms.
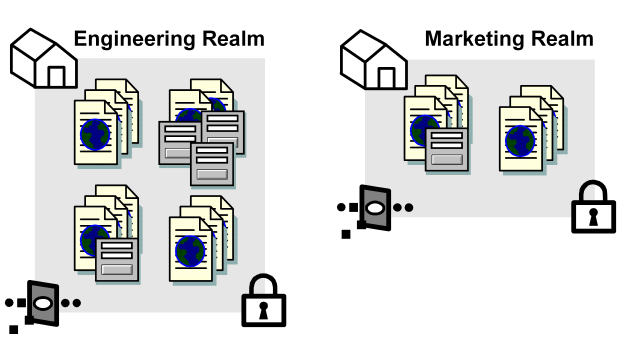
Each of the realms contains web service resources. In addition, each realm is associated with a SOA Agent and an authentication scheme.
A realm is usually defined for resources that reside in a common location on your network. For example, web services that process incoming purchase orders and are bound to URLs in an /Orders directory or accessible by an Orders JMS queue might be configured as a realm in a policy domain managed by an administrator in a company’s order fulfillment organization. The realm also specifies the authentication scheme to be used. Typically, you should create a realm for each web service (as defined by a WSDL port element).
Web service resources are identified in the realm according to whether they will be accessed by HTTP(S) or JMS transports as follows:
Also, choose a SOA Agent to protect these resources and bind these resources to the same authentication scheme
| Copyright © 2011 CA. All rights reserved. | Email CA Technologies about this topic |