Token Subject and Issuer Confirmation and Validation
The WS‑Security authentication scheme can use multiple aspects of an incoming SOAP document to validate the subject and issuer of a SAML token:
The exact manner in which the authentication scheme assertion subject and issuer are validated depends on the subject confirmation method that you specify. SOA Security Manager supports both methods defined in the Web Services Security SAML Token Binding specification.
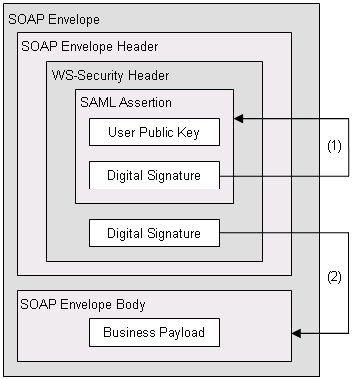
The holder-of-key method confirms that the subject of the SAML token and the sender of the request containing that token have the same identity, mandating the following:
SAML tokens with the holder-of-key subject confirmation method are reusable. That is, when returned to the web service consumer (as in the multistep authentication method), a holder-of-key SAML token can subsequently be associated with other SOAP documents—not just with the document sent to the authentication service. This allows the web service consumer to send one request to the authentication service and then associate the returned token with multiple documents and send them directly to target web services.
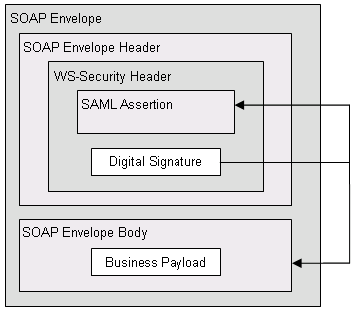
The sender-vouches method confirms that the subject of the SAML token was authenticated by the trusted token issuer, which vouches that the identity of the token’s subject is the web service consumer making the request. The token issuer then binds the assertion and the message body together by signing them with its private key.
Note: The sender-vouches token is valid only in association with the SOAP document to which it is bound by the authentication service—it cannot be reused with other documents.
The identity of the token issuer can be validated during authentication by doing the following:
The main distinction between these validation mechanisms is that the digital signature mechanism requires signed elements within the message being processed. When using the SSL case, you can improve security by configuring SOA Security Manager to obtain the token issuer’s client certificate from the link and use it to validate against the Smkeydatabase.
The following table provides a complete summary of the security features and associated validation methods available for messages using the different subject and issuer confirmation methods.
|
Confirmation Method |
Message Security Features |
Subject/Issuer Validation Method |
|---|---|---|
|
Holder-of-key |
The web service consumer’s authenticated ID is the subject of the SAML assertion token (default, alternative subject can be specified using an explicit XPath statement); subject’s public key/certificate is included in the assertion. The SAML token issuer signs the assertion using its certificate/public key. The assertion content is signed by the subject and is validated based on the fact that the user is the holder of the private key that corresponds to the public key in the assertion that is used to verify the content signature. |
Assertion subject is validated against an associated user directory Token subject’s public key/certificate is validated against the Smkeydatabase. Token issuer’s public key/certificate is validated against the Smkeydatabase. |
|
Sender-vouches with signature-based issuer validation |
The web service consumer’s authenticated ID is the subject of the SAML assertion token (default, alternative subject can be specified using an explicit XPath statement); subject’s public key/certificate is not included in the assertion. The SAML token issuer signs the assertion. The SAML token issuer also signs the complete SOAP document. |
Assertion subject is validated against an associated user directory Token issuer’s public key/certificate is validated against the Smkeydatabase |
|
Sender-vouches with |
The web service consumer’s authenticated ID is the subject of the SAML assertion token (default, alternative subject can be specified using an explicit XPath statement); its public key/certificate is not included in the assertion. The SAML token issuer is the holder of the client certificate and private key used to set up the SSL connection. |
Assertion subject is validated against an associated user directory. The token issuer and content, including the SAML token, are implicitly validated by being encrypted and decrypted over SSL using SSL encryption keys derived from the issuer’s client and server certificates used to set up the SSL link. That is, the encryption may be thought of as a form of the client certificate indirectly signing the content. The token issuer’s public key/certificate can be validated against the SSL key store on the web server or the Smkeydatabase. |
Note: Sender-vouches with SSL-based issuer confirmation is weaker than sender-vouches with signature-based issuer validation. With signature-based issuer validation, each message is protected by the holder of the issuer private key, whereas in the SSL case only the channel is protected by the holder of the issuer private key. This means if an intruder gets access to the channel, anything sent on that channel is considered valid; whereas, in the general case the intruder would have to actually get access to the issuer private key itself to sign individual messages.
| Copyright © 2011 CA. All rights reserved. | Email CA Technologies about this topic |