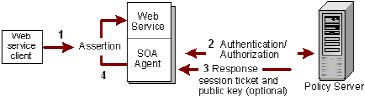
The SAML Session Ticket response provides the data that the SOA Agent uses to create an assertion. The only authentication scheme that can evaluate the assertion is the SAML Session Ticket authentication scheme.
When an XML assertion document arrives at a web service protected by the SAML Session Ticket authentication scheme, the SOA Agent does the following:
The binding of the session ticket and the public key ensures that the XML document is signed by a client that is authenticated by SOA Security Manager and that has a valid session.
Then, if the Agent does not have the session ticket in its cache, the Policy Server validates the client with the session ticket from the assertion. If the Agent does have the session ticket in its cache, the Policy Server is not invoked.
Note: The web service that returns the assertion is not protected by the SAML Session Ticket authentication scheme. Only subsequent services in the single sign-on environment require this authentication scheme.
The following illustration shows the response process.
| Copyright © 2011 CA. All rights reserved. | Email CA Technologies about this topic |