Federation Manager Agent for Windows Authentication Guide › Introduction to the CA Federation Manager Agent for Windows Authentication › Kerberos Protocol
Kerberos Protocol
The Kerberos protocol is an elaboration of the NTLM protocol. The following illustration shows how Federation Manager and the Federation Manager Windows Agent use the Kerberos protocol:
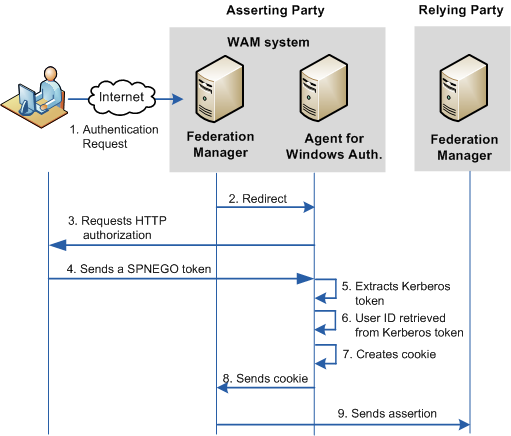
The following process references annotations in the preceding diagram:
- An authentication request is made to Federation Manager at the asserting party.
Federation Manager recognizes that this request is a delegated authentication request.
- Federation Manager redirects to the Federation Manager Windows Agent.
- The Federation Manager Windows Agent requests an HTTP authorization from the browser.
- If the browser is configured for IWA, it sends a SPNEGO token to the Federation Manager Windows Agent. This token allows initiators and acceptors to negotiate whether to use Kerberos or NTLM.
- The Federation Manager Windows Agent extracts a Kerberos token from the SPNEGO token.
- After the security context is established from the Kerberos token, the Agent retrieves the user identity information.
- The Agent creates the open format cookie and builds a redirect URL.
- The Agent sends the cookie to Federation Manager.
- Federation Manager does the required processing and sends an assertion to the relying party.
