The following diagram shows a typical CA Audit network with CA Enterprise Log Manager added to leverage its high volume event handling and compliance-based reporting capabilities:
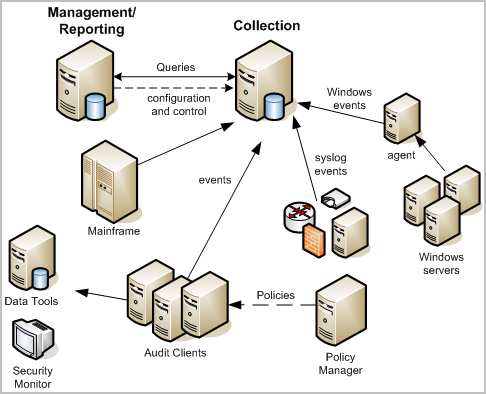
CA Enterprise Log Manager uses an integrated Agent Explorer, an embedded event log store, and single user interface to centralize and simplify log collection. CA Enterprise Log Manager agent technology coupled with the common event grammar allows for faster event throughput to storage while handling a higher number of event sources. A single agent can handle multiple connectors to event sources, simplifying agent management tasks, and taking advantage of predefined integrations for popular or common event log sources.
In this implementation, the CA Enterprise Log Manager collection server receives the syslog, iTechnology-based, and SAPI recorder events directly. The collection server receives events from Windows event sources through a separate Windows-based CA Enterprise Log Manager agent. You may have several agents deployed in your network, each of which can gather many different kinds of event data through its connectors. This can help to reduce event traffic to the SEOSDATA database and leverage the queries and reports available in CA Enterprise Log Manager. A simple policy rule change allows the CA Audit clients to send collected events to both the Data Tools server and the CA Enterprise Log Manager server.
In addition to higher throughput, CA Enterprise Log Manager offers out-of-the-box queries and reports that help you to demonstrate compliance with regard to multiple standards like PCI (DSS) and SOX. When you couple the predefined queries and reports with your existing CA Audit and CA SCC implementation, you can leverage your investments in your custom solutions while taking advantage of CA Enterprise Log Manager reports and higher throughput.
| Copyright © 2011 CA. All rights reserved. | Email CA Technologies about this topic |