When you create a policy based on an existing policy, you copy the existing policy and save it to a new name. Then, you rename it, edit the description to fit the new role, and replace the existing identities with your new identity. When the policy you are using as a template provides access that is too broad for your new role, you create filters to limit that access.
For the PCI-Analyst scenario, you copy the Analyst Report View-Edit policy, save it to a new name, open the new policy, replace the identity with the PCI-Analyst group, and add a filter to limit report access to those reports tagged with the PCI calmTag.
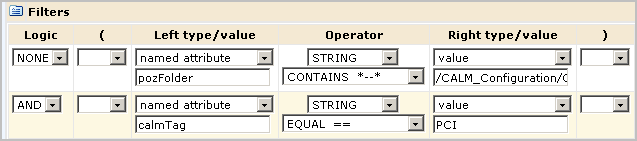
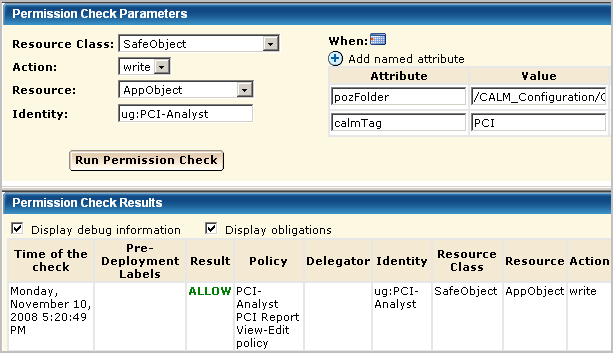
It is a good practice to test a policy based on an existing policy just as you would a policy you created from scratch. When you test a policy with a filter, be sure to enter the filter exactly as it is entered in the policy. When you enter a group name for identity, be sure to prefix it with ug:, for example, ug:PCI-Analyst.
| Copyright © 2011 CA. All rights reserved. | Email CA Technologies about this topic |